In cybersecurity, organisations use security frameworks and controls to protect against threats, risks, and vulnerabilities. Frameworks include the NIST Risk Management Framework (NIST RMF), the Cybersecurity Framework (CSF), the CIA triad, and others.
Most of the security framework can be applied to any organisation, regardless of its size (small, mid-sized, or large), to protect its assets, data, and operations.
Different frameworks apply to various sectors, such as HIPAA for healthcare and PCI DSS for finance. Organisations can tweak the security framework to make it easier or more suitable for themselves.
In this article, we will discuss security frameworks and controls, and how they work together to mitigate risk to the organisation.
Advantages of using security frameworks
Security frameworks provide a step-by-step guide to manage and improve security from upcoming threats, risks, and vulnerabilities. These are also known as the first line of defence in cyberspace.
Advantages are:
- Consistency: Since they provide a standardised set of guidelines and best practices, which help organisations implement security measures.
- Fundamental: These frameworks are so in-depth, well-documented, and very close to being perfect. By implementing these, organisations don’t have to remake the security policy, which saves time, money and resources.
- Trustworthy: Some of the frameworks were created in the presence of government officials and industry experts to demonstrate the security of data, which helps build trust with stakeholders, clients, and partners.
Security Frameworks
Security frameworks serve as guidelines or rules used in building plans to help mitigate risks and threats to data and privacy. It supports an organisation’s ability to comply with laws and regulations.
For example, the healthcare industry uses frameworks to comply with the United States’ Health Insurance Portability and Accountability Act (HIPAA), which mandates that medical professionals safeguard patient information and maintain their identity secure.
Security Controls
Security controls are safeguards designed to reduce specific security risks. Security controls are the measures organisations use to lower risk and threats to data and privacy.
For example, an organisation can use a control alongside frameworks to ensure a hospital remains compliant with HIPAA by requiring patients to use multi-factor authentication (MFA) to access their medical records.
Using a measure like MFA to validate someone’s identity is one way to help mitigate potential risks and threats to private data.
Examples of physical controls:
- Gates, fences, and locks
- Security guards
- Closed-circuit television (CCTV), surveillance cameras, and motion detectors
- Access cards or badges to enter office spaces
Examples of technical controls:
- Firewalls
- MFA
- Antivirus software
Examples of administrative controls:
- Separation of duties
- Authorisation
- Asset classification
CIS Controls
The company, the Center for Internet Security (CIS), has already published 18 security practices, known as CIS Controls.
It helps to plan security strategies and cover implementation, incident handling, monitoring and training.
CIS controls are categorised into three sections: introductory, foundational, and organisational. This categorisation will help you prioritise your tasks.
Here are the CIS controls:
| Account management | Data protection |
| Inventory and control of enterprise assets | Audit log management |
| Continuous vulnerability management | Inventory and control of software assets |
| Secure configuration of enterprise assets | Application software security |
| Data recovery | Access control management |
| Network monitoring and defence | Malware defences |
| Email and web browser protections | Network infrastructure management |
| Incident response management | Penetration testing |
| Service provider management | Security awareness and skills training |
Cyber Threat Framework (CTF)
The U.S. government established the CTF to offer “a common language for describing and communicating information about cyber threat activity,” according to the Office of the Director of National Intelligence.
The CTF encourages more effective information analysis and sharing among cybersecurity professionals by offering a consistent language for sharing information about threat behaviour. This enables organisations to better respond to the ever-changing cybersecurity environment and the many strategies and methods used by threat actors.
Health Insurance Portability and Accountability Act (HIPAA)
The HIPAA is a structured guideline used in the healthcare sector. The focus of this framework is to protect medical records and health data.
It provides best practices for securing healthcare information, training individuals, and conducting risk assessments.
The major challenge with this framework is keeping up with technology, as HIPAA doesn’t support it properly. The HIPAA is mandatory for both healthcare organisations and insurance companies.
Organisations can get HIPAA certification by meeting the standards set for these major rules:
- Privacy
- Security
- Breach notification
- Omnibus
- Enforcement
International Organisation for Standardisation (ISO) 27001
The family group of ISO 27000 (different frameworks) caters for all sectors and sizes of organisations to manage assets such as financial information, intellectual property, employee data and information entrusted to third parties.
ISO 27001 is recognised internationally and used commonly in organisations across the world.
This framework fulfils the requirements for an information security management system, including best practices and controls that help manage risk for an organisation.
The ISO 27001 framework does not require the use of security controls, but provides an extensive collection of controls that can help improve an organisation’s security posture.
MITRE ATT&CK Framework
The MITRE ATT&CK Framework is one of the most comprehensive cybersecurity frameworks, covering a wide range of strategies, methods, and processes. It offers guidance for identifying and stopping cybersecurity threats based on the known adversary behaviours of cyber criminals.
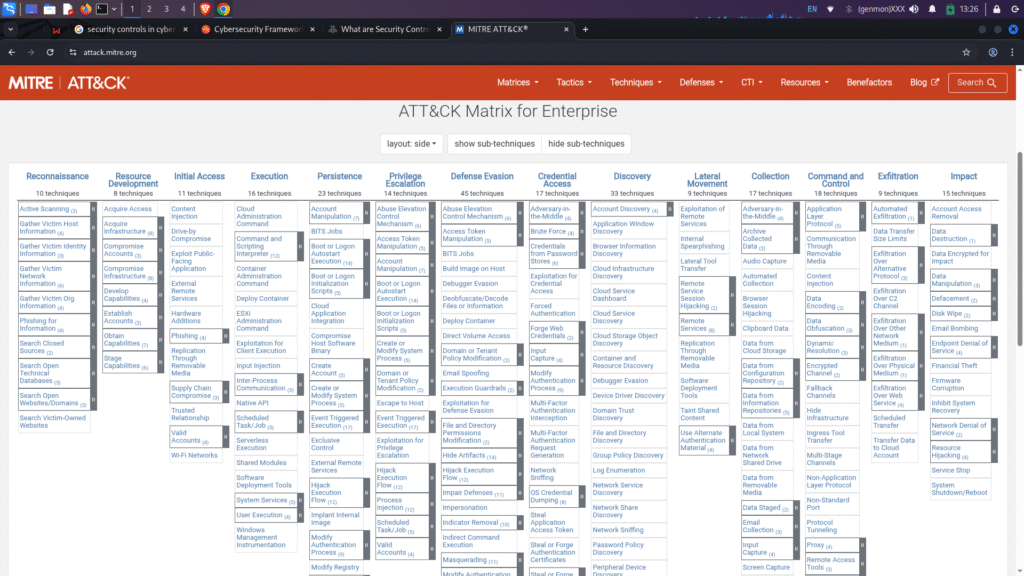
The MITRE ATT&CK Framework is divided into three matrices: Enterprise, Mobile, and Industrial Control Systems (ICS).
These strategies are covered under the framework:
| Reconnaissance | Credential access |
| Resource development | Discovery |
| Initial access | Lateral movement |
| Execution | Collection |
| Persistence | Command and control (C2) |
| Privilege escalation | Exfiltration |
| Defense evasion | Impact |
Conclusion
Cybersecurity frameworks and controls are used together to establish an organisation’s security posture. They also support an organisation’s ability to meet security goals and comply with laws and regulations.
Although these frameworks and controls are typically voluntary, organisations are strongly encouraged to implement and use them to help ensure the safety of critical assets.


