In the digital age, users increasingly prefer to conduct various activities online, including making friends, shopping, watching movies, and banking. These online facilities offer convenience but also carry a significant risk. One of the main risks is a Phishing attack.
Phishing sounds and works exactly like Fishing. But how? Fishing means catching fish. How will it be similar to Phishing? Let me explain….
In Fishing, a person goes to the river and catches fish with a fishing rod. The person will lure the fish using worms as bait attached to the fishing rod. The fish will be hooked on the fishing rod.
In comparison to Phishing, an attacker emails the user with a fake link. For example, the email is about a sale on Amazon and wants the user to log in. The attacker will lure the user into logging in to a fake Amazon website. Then those credentials will be on the attacker’s screen.
Yes, the meaning of both terms, Phishing and Fishing, is the same, just the difference in the scenario.
Phishing is not just about emails. It has multiple forms, which we will learn later on.
Let’s take a deep dive and understand how Phishing works, as it is one of the most successful cyber-attacks.
History
Phishing originated in the mid-1990s, when cyber criminals began impersonating AOL to obtain customer login information. This attack was straightforward for the users to verify their accounts.
The tactics have changed over time, from basic spam to sophisticated, targeted attacks known as spear phishing.
Spear phishing uses personalised information to target specific individuals or organisations.
Why is this Dangerous?
This attack is dangerous as it plays psychological and emotional tricks to lure the victim. A single click on a malicious link can:
- Compromise sensitive data
- Leads to identity theft
- Financial losses
- Give attackers access to corporate networks.
- It can damage an organization’s reputation and stock.
Different forms
Phishing is a method of social engineering that involves stealing credentials from users through various channels, including messages, calls, emails, and social media.
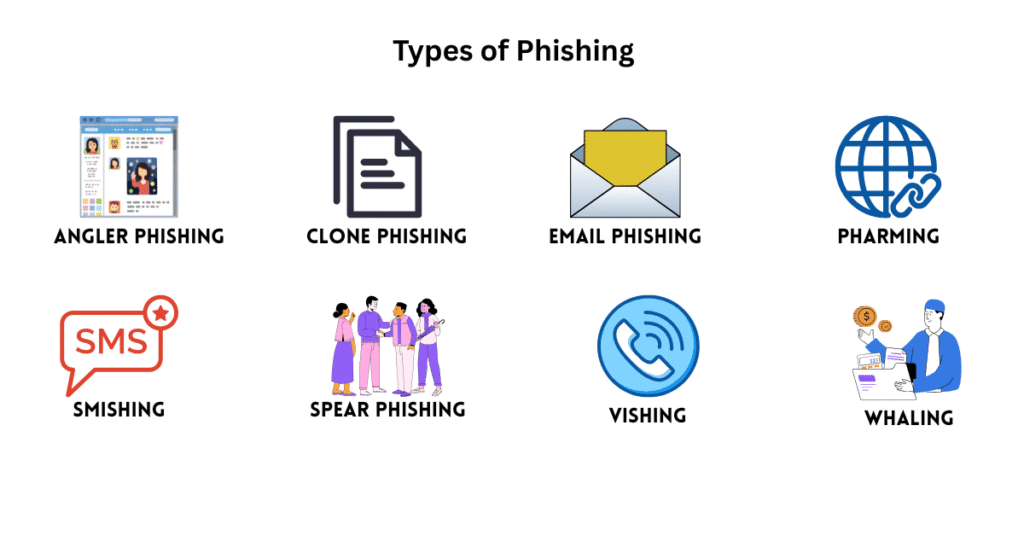
Usually, cyber attackers use a job or a sales campaign to lure victims into their trap.
- Angler Phishing
Angler phishing is a scam that targets the victim through social media. Attackers create fake accounts that mimic genuine customer service or products. This technique deceives consumers into thinking they are speaking with authorised staff by taking advantage of the trust that exists in brand-customer interactions on these platforms.
- Clone Phishing
Clone phishing is a method of duplicating an already delivered email with a malicious link or attachment, with the original one. The victim may think the attachment is safe as it came from the legitimate sender. However, the attachment could easily lead to a malware attack.
- Email Fraud
Email fraud is one of the easiest attack models, which is simple to execute. To execute this attack, an attacker has to send fraudulent emails in bulk to target a broad audience of individuals or a specific organisation. Users with limited knowledge are at risk of falling into this trap, which could lead to a significant data breach.
- Pharming
Pharming is a method of manipulating the Domain Name System (DNS) to redirect users from legitimate websites to a fake one without their knowledge. This way, the attacker can distribute malware-injected software, and users may think it’s a legitimate and safe software.
To protect against the subtle manipulations of pharming, awareness and secure, authenticated connections are essential.
- Smishing
Smishing is also known as SMS Fraud. In this attack, an attacker tricks the victim through text messages to click on malicious links or disclose personal information.
They will create an alert message that appears to be from a bank or government agency, aiming to provoke immediate action. Smishing takes advantage of the broad trust in SMS communication by sending users to harmful websites or urging the submission of sensitive data.
- Spear Phishing
Spear phishing is a type of attack where the attacker uses personal or organisational information to craft convincing messages. The attacker may research their targets to make their message more relevant and trustworthy. This attack is particularly harmful and challenging to detect due to its high level of customisation and intimate character.
- Vishing
In a vishing attack, the attacker uses phone calls to impersonate a representative of a company, such as a bank, insurance company, or government agency.
They aim to obtain personal information from the victim by creating a false sense of urgency over the phone. Fake call centers typically conduct vishing attacks for financial gain.
- Whaling
Whaling is an advanced version of spear phishing. In this case, the attacker may target high-profile individuals, such as CEOs, politicians, and celebrities, due to their influence and value among the general public. These high-profile individuals are also known as “Big Fish.”
Attackers must invest a significant amount of time researching their target’s well-known personalities. They need to review corporate websites and social media to make their message more convincing.
This degree of personalisation and intricacy is intended to deceive recipients into disclosing sensitive information or authorising financial transactions, leveraging their position within their organisations or public standing.
Example 1
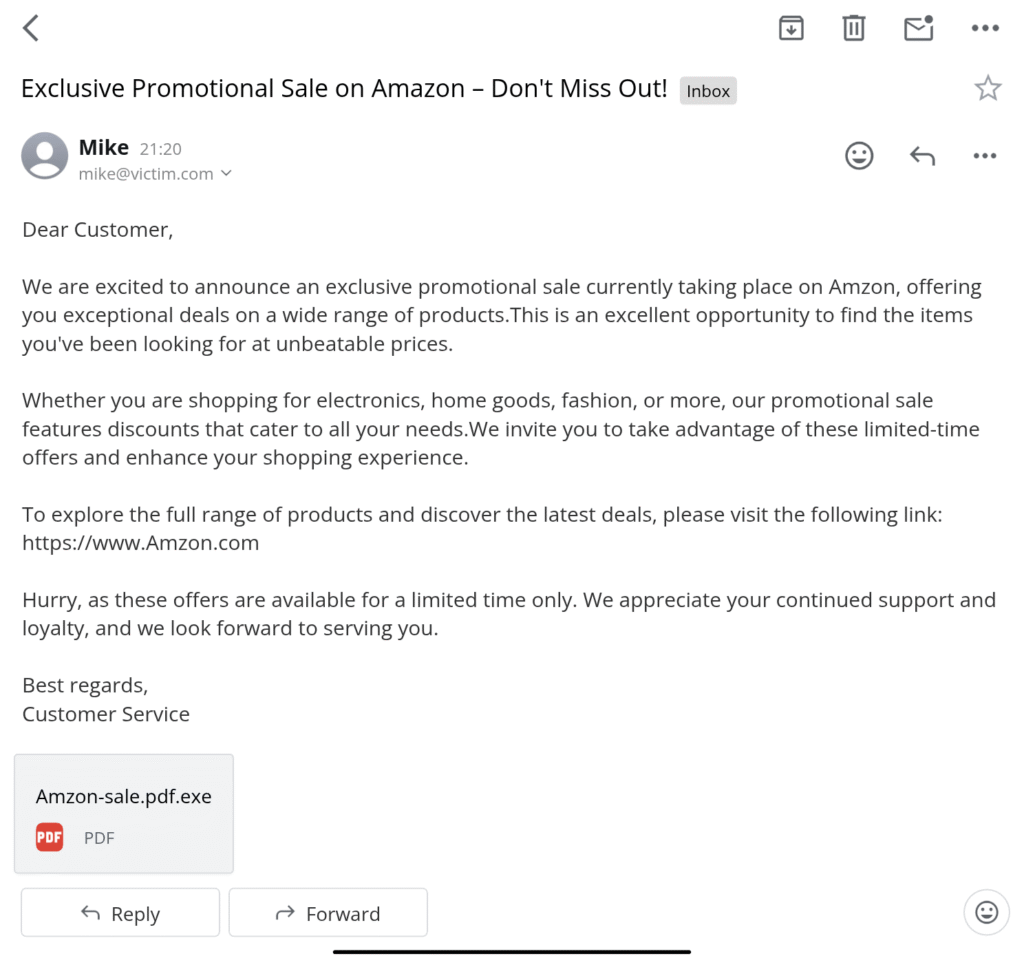
The above screenshot is an example of an Email Scam. We can see several signs that the email is not from the original company. Can you find the clues? If you did, tell us in the comments section how many you got?
The clues are:
- Attachment: If you notice the attachment file, a normal user might assume it’s a standard PDF list of sale products, but it’s an executable file (.exe) that could be malware or ransomware.
- Generic Greeting: The company has an email list of customers. There’s no chance of an email without the customer’s name.
- Spelling Mistake: If you notice in the email, the name of the company is not correct.
Example 2
This one is the real phishing email that I received in my Gmail. If you can see the email provider, I’ve already flagged it as spam, and it has a warning of “This message might be dangerous”.
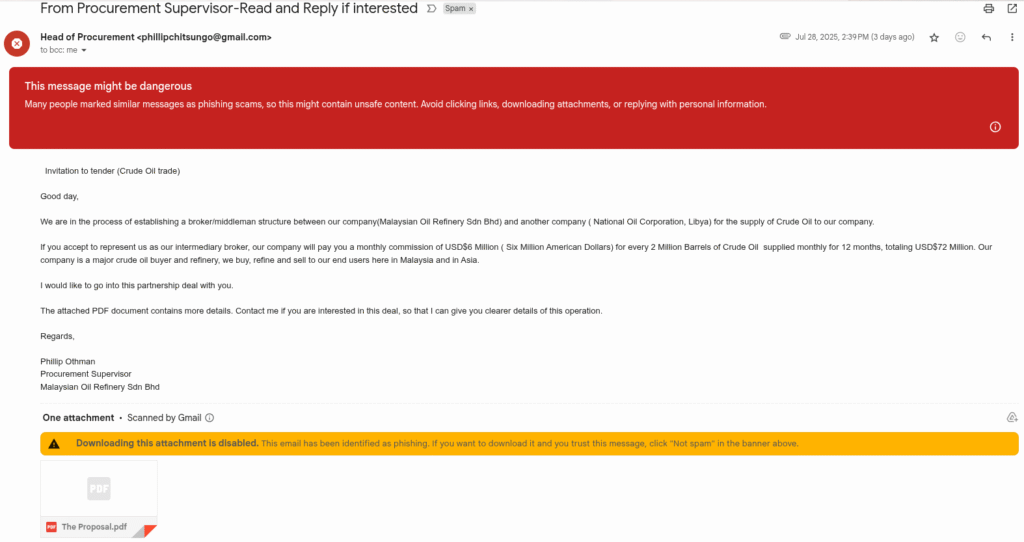
This email is an invitation for an oil contract. The scammer is trying to impersonate a representative from Malaysian Oil Refinery Sdn Bhd, a legitimate company.
The clues are:
- Generic Greeting: If he wants to offer any work, he should know me or my work. They have to greet me by name.
- Flagged: My email provider has already automatically warned me that this could be dangerous.
- Attachment: The PDF content is identical to the email content, with no additional information.
- Finance: In this era, no one gives money to the company worker, but they are offering $6 million to make people greedy and get trapped.
How to Identify a Phishing Attempt?
Below are the few red flags to watch out to spot a phishing attack:
| Red Flag | What it Means |
|---|---|
| Urgent or Alarming language | Pressuring to act fast (such as account locked, someone logged-in) |
| Generic Greeting | Instead of your name, using “Dear customer” or just “Hi”. |
| Suspicious links or Attachments | Embedded unnecessary links or attachment. |
| Grammar/Spelling Errors | Check spelling such as company name, inside the paragraphs. |
| Request for sensitive info | Real companies never ask personal info through emails or message. |
How to Protect Yourself?
- Think Before You Click
Before clicking any link, consider whether you are waiting for an email or message, such as an OTP, Location, document, or verification, and so on.
If not, don’t click and always verify it.
- Use Multi-Factor Authentication (MFA)
MFA or 2FA is a setup that enhances account security. Even if someone has your password, they can’t access your account without the MFA code. There are two applications available: Microsoft Authenticator and Google Authenticator.
- Keep Software Updated
Regularly check and update the software, so attackers may not have a chance to exploit you.
- Install Antivirus and Firewalls
These tools can warn you about risky websites and detect malicious files.
- Verify the Sender
If you receive a suspicious message, contact the company directly and verify if they sent it to you.
- Report it
Every email provider allows you to report Phishing. Reporting helps improve overall security.
Conclusion
Phishing is more than just an annoying email. It’s a powerful and dangerous attack used by cyber attackers to manipulate and exploit individuals and organizations.
Being able to identify and avoid Phishing is a critical skill in today’s digital world.
Whether you’re an individual checking email or an IT manager protecting company data, awareness is key.
Always verify, never rush, and when in doubt, throw it out.
Resources
What is Phishing?: Risks and Prevention in the Digital Age


