Steghide is one of the best tools used for steganography. This tool was created by Stefan Hetzl in the year of 2003. Steghide is used to hide or embed files in images and audio. It uses a passphrase (any kind of password) to embed and extract private files.
This tool is an easy, beginner-friendly, and configurable tool. The best thing about this tool is that it’s available for Linux and Windows.
Steghide supports various formats for input such as PNG, JPG, JPEG, and BMP for images and AU and WAV for audio as the cover file. An image or audio file which is the mediator to hide the main file is known as a cover or stego file. There are no restrictions on the format of the embedding file. By default, it uses the Rijndael algorithm and the key size of 128 bits.
How to install steghide on Linux?
This tool is not pre-installed in both Kali Linux or Parrot Security OS. We will see how to install it.
sudo apt-get install steghide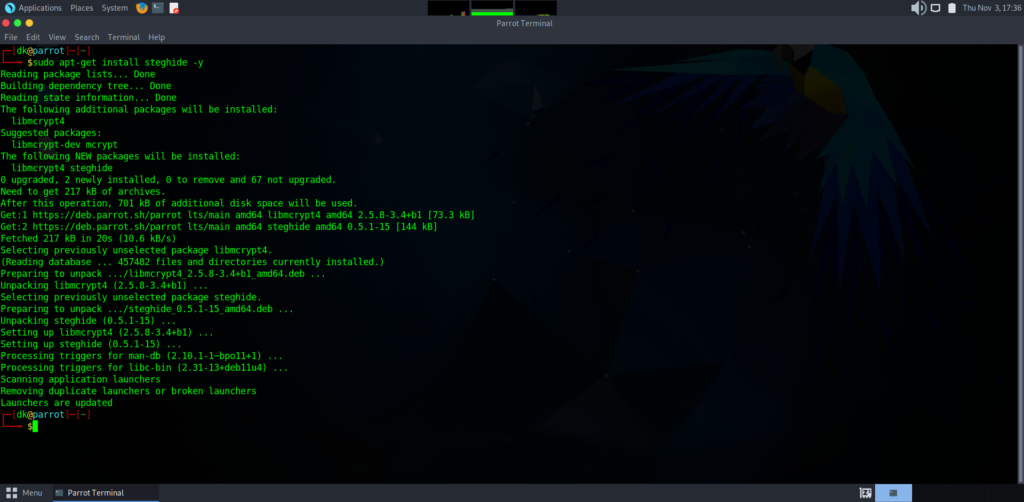
Let’s check, the steghide installed.
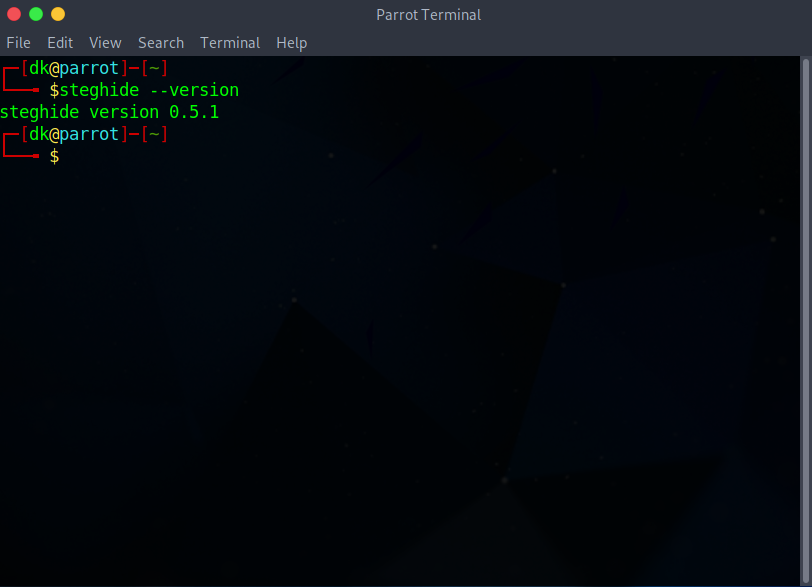
How to install steghide on Windows?
Go to the Steghide SourceForge website. Here you can download the steghide package for Linux and Windows.
Click on the Windows package, which will redirect to the SourceForge page and automatically downloads it.
Options or Parameters
The first parameter after steghide must be one of the following:
embed, –embed: This is used to embed data of one file into another.
extract, –extract: This is used to extract data from the file.
info, –info: This is used to display information about a cover- or stego-file.
info <filename>: This is used to display information about <filename>. It can be a cover file or a file to be embedded. With this option, you can know whether the tool supports that file type or not.
encinfo, –encinfo: It will display a list of supported encryption algorithms.
version, –version: It will display the current version.
license, –license: It will display steghide’s license
help, –help: It will display the list of information about all the options or parameters.
The options to embed:
-ef, –embedfile: To select the file to be embedded.
-ef <filename>: To embed the file by giving the location and name of the file.
-cf, –coverfile: To select cover-file or stego-file.
-cf <filename>: To give the location and name of the cover or stego file.
-p, –passphrase: To give passphrase. It’s a password used to embed and extract the file
-p <passphrase> use <passphrase> to embed data
-sf, –stegofile select stego file
-sf <filename> write result to <filename> instead of cover-file
-e, –encryption select encryption parameters
-e <a>[<m>]|<m>[<a>] specify an encryption algorithm and/or mode
-e none do not encrypt data before embedding
-z, –compress: compress data before embedding (default)
-z <l> using level <l> (1 best speed…9 best compression)
-Z, –dontcompress does not compress data before embedding
-K, –nochecksum do not embed crc32 checksum of embedded data
-N, –dontembedname do not embed the name of the original file
-f, –force overwrite existing files
-q, –quiet suppress information messages
-v, –verbose display detailed information
Extracting options:
-sf, –stegofile select stego file
-sf <filename> extract data from <filename>
-p, –passphrase specify passphrase
-p <passphrase> use <passphrase> to extract data
-xf, –extractfile select file name for extracted data
-xf <filename> write the extracted data to <filename>
-f, –force overwrite existing files
-q, –quiet suppress information messages
-v, –verbose display detailed information
Options for the info command:
-p, –passphrase specify passphrase
-p <passphrase> use <passphrase> to get info about embedded data
The basic command to embed emb.txt in cvr.jpg: steghide embed -cf cvr.jpg -ef emb.txt
The basic command to extract embedded data from stg.jpg: steghide extract -sf stg.jpg
How to hide and extract text files in an image?
We have two prerequisites to use this tool. They are cover file and secret file.
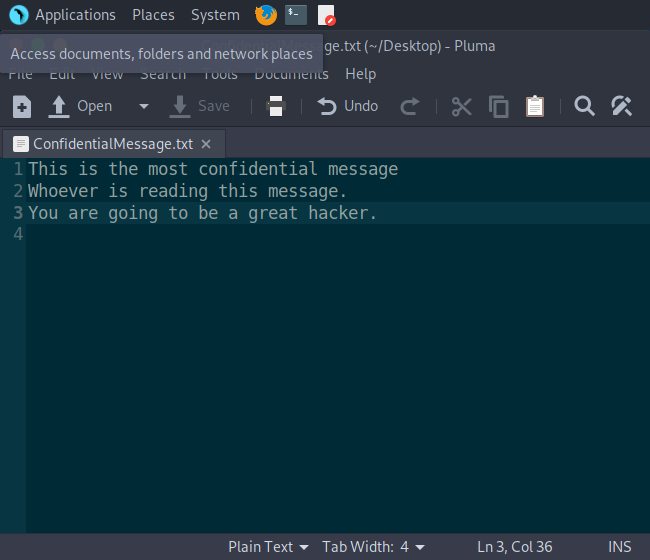

Linux
You can try it on any Linux distribution such as Kali Linux, Parrot Security OS, Ubuntu, or any other distribution. Now, we will see how to hide text files in the image on Parrot Security OS. The steps are the same for Kali Linux.
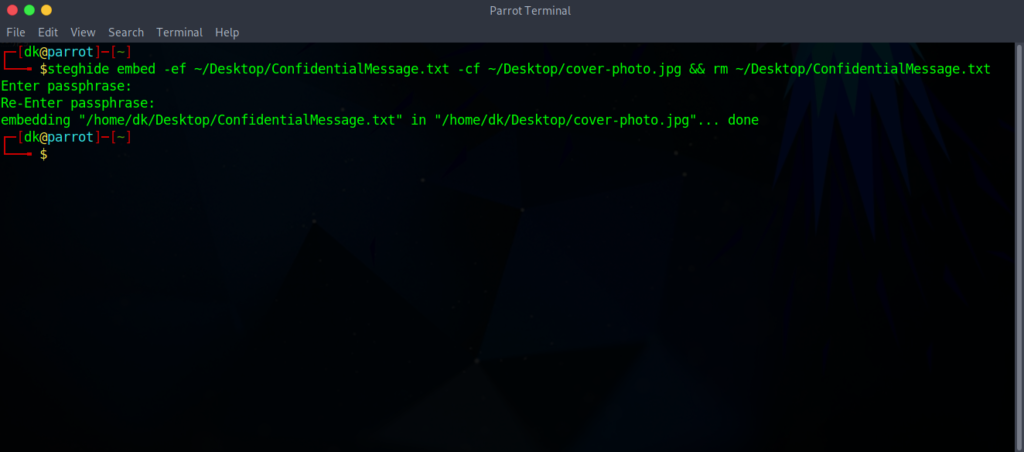
To embed the data:
Now, we will execute the command shown below. The terminal asks to enter and re-enter the passphrase. After that, it will be embedded successfully.
To extract the data:
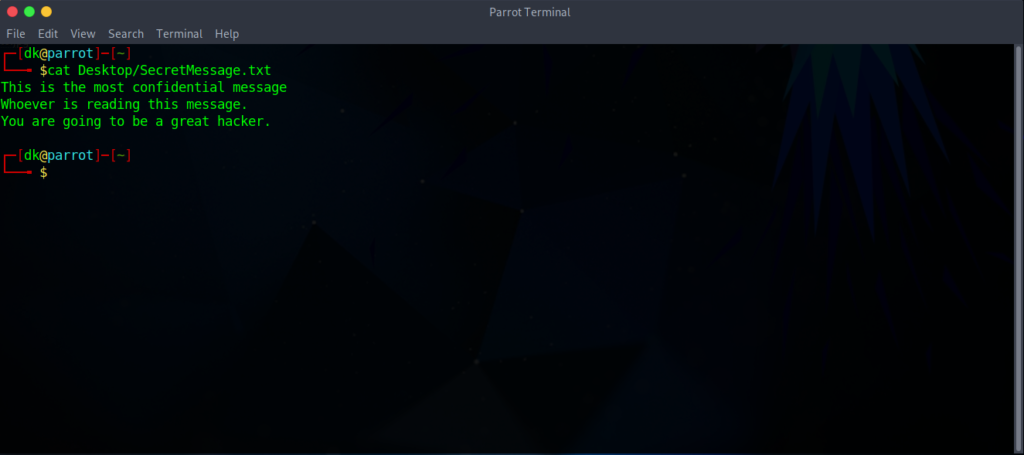
We will execute the command shown below. The terminal will ask for the passphrase (we enter during embedding the file) to enter.

Here is the result that proves, it recovers the file successfully.
Windows
Steghide is one of the tools which is available for windows also. You can only use this tool in CLI mode in CMD.
Conclusion
Steghide is one of the best and easy tool for steganography. This tool is very useful in CTF competition. The main cons of this tool is that it doesn’t supports any of the video formats. But it is good for audio and image formats. This tool is very old but very useful and popular till date.


