Snort is a widely used open-source intrusion detection system (IDS) that monitors network traffic for suspicious activity and logs the event when it detects something unusual.
These log files are key to understanding what’s happening in your network — but only if you know how to read them. Tools like tcpdump and Wireshark make this job easier by helping you visualize and interpret the raw data.
In this guide, we’ll explain how to read Snort log files using tcpdump and Wireshark so you can investigate alerts effectively and better protect your network.

Understanding Snort Log Formats
Before diving into analysis, you must know what format Snort uses to log its data. Snort supports several output formats:
- Unified2: Binary log format (preferred for performance and compatibility).
- pcap: Packet capture format used by tools like tcpdump and Wireshark.
- Alert logs: Human-readable alerts (in /var/log/snort/alert or similar).
- Fast/Full Alerts: Text-based alerts with varying verbosity.
For tcpdump and Wireshark, we’re primarily interested in pcap or unified2 logs. Snort, which is set to log packets (not just alerts), will find .pcap files in the log directory.
Step 1: Configure Snort to Log Packets
Make sure Snort is capturing packets, not just generating alerts. In the Snort configuration file (snort.conf), you should see a line like: output log_tcpdump: snort.log
The second way, you can run Snort with the -b option to create binary logs:
snort -i eth0 -c /etc/snort/snort.conf -b -l /var/log/snortThis command logs binary data into files like snort.log.xxxxxxxxxx.
Step 2: Reading Snort Logs with tcpdump
The tcpdump command is helpful for quickly looking into Snort’s log files. It’s lightweight and runs right in the terminal.
Example: Viewing a Snort log file
Assuming Snort created a .pcap or binary log file like snort.log.1682451234, use:
tcpdump -r /var/log/snort/snort.log.1425743287.pcap
This will display each packet’s timestamp, source and destination IPs, protocol, and ports.
Filtering with tcpdump
To narrow down what you’re looking for:
- Filter by IP:
tcpdump -r snort.log.1682451234 host 192.168.1.10 - Filter by port:
tcpdump -r snort.log.1682451234 port 80 - Filter by protocol:
tcpdump -r snort.log.1682451234 icmp
This is especially helpful when hunting for a specific attack or behavior.
Converting Binary Log to pcap
If Snort logs are in unified2 format, convert them to pcap with u2boat or barnyard2:
u2boat -r snort.log.1682451234 -w output.pcapOnce converted, you can open output.pcap in Wireshark.
Step 3: Opening Snort Logs in Wireshark
Wireshark is a powerful GUI tool that simplifies packet analysis through color coding, protocol dissection, and filtering.
Opening a pcap File
Launch Wireshark and open your log file via:
Step 1: Go to File
Step 2: Click Open
Step 3: Choose the right file such as snort.log.1682451234 (or any .pcap file)
You’ll immediately see a list of packets, timestamps, IPs, protocols, and lengths. Click any packet to expand the protocol layers.
Using Wireshark Filters
Wireshark supports a wide range of display filters. Here are some useful ones:
- ip.addr == 192.168.1.10 — Filter packets with a specific IP.
- tcp.port == 80 — Show only HTTP traffic.
- http — Show only HTTP packets.
- icmp — Filter for ping packets.
- tcp.flags.syn == 1 and tcp.flags.ack == 0 — Show TCP SYN (possible scans).
These filters help isolate suspicious traffic quickly.
The screenshot below reads the pcap file through Wireshark with the ICMP filter.
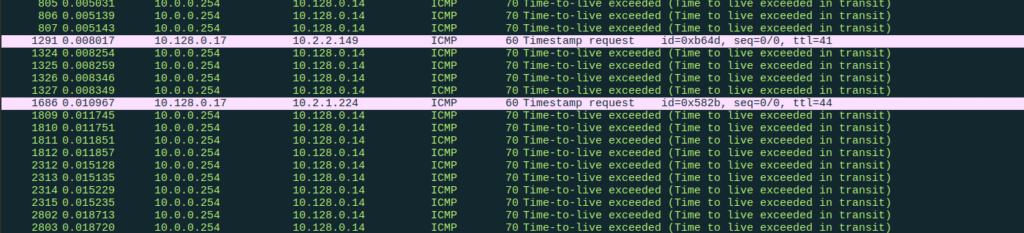
Analyzing a Suspicious Packet
Let’s say Snort triggered an alert on a port scan. Open the corresponding pcap in Wireshark and use: tcp.flags.syn == 1 and tcp.flags.ack == 0
This shows all SYN packets, which are often used in scans. Look for patterns like multiple destination ports from a single source IP — a strong sign of reconnaissance.
You can right-click on a packet and select Follow TCP Stream to reconstruct conversations, which can help you understand exploits or payload delivery.
Bonus: Combining tcpdump and Wireshark
Use tcpdump to create your own packet captures and analyze them in Wireshark:
tcpdump -i eth0 -w capture.pcapThen open capture.pcap in Wireshark for detailed inspection.
Tips for Efficient Snort Log Analysis
- Correlate logs: Use Snort alerts to zero in on which packet captures to investigate.
- Use filters: Both tcpdump and Wireshark allow precise filtering, which saves time.
- Automate: Consider using Barnyard2 to process unified2 logs and forward alerts.
- Watch timestamps: Correlate packet times with alert logs to find the right packets.
- Log rotation: Snort logs can get big fast — make sure you rotate and archive them.
Final Thoughts
Snort gives you the detection power, but tools like tcpdump and Wireshark make that data usable. Reading Snort logs with these tools helps you spot patterns, investigate incidents, and harden your network against future attacks.
If you’re just starting out, focus on recognizing basic protocol behaviors and how attacks typically look on the wire. You’ll get faster and sharper at identifying threats from raw packet data with practice.


