Naabu is a fast port scanner written in the go programming language. It focuses on reliability and simplicity. This tool is created and managed by Project Discovery.
It is a very straightforward program that quickly checks the host or list of hosts using SYN/CONNECT and reports all ports that only respond. Because of the speed, it saves a lot of time for the users.
Features Of Naabu Tool
- Fast Scanning: Naabu has been streamlined for speed and can quickly scan hundreds of hosts and ports.
- Customizable Scanning: Users of Naabu can alter the scanning settings, such as the port range, the top ports, and the timeout value.
- Modular Design: Users may build their scanners, and add additional features and capabilities to Naabu’s modular architecture.
- Extensive Reporting: Naabu produces thorough reports with information about open ports, HTTP and HTTPS servers, and discovered vulnerabilities.
- Flexible Output Formats: Users of Naabu can select from a variety of output formats, including JSON, XML, and CSV.
- Simple Setup: Naabu is simple to set up and needs very little configuration.
- Nmap Integration: Users can easily integrate Nmap into the tool.
Use Cases for Naabu Tool
Many network reconnaissance and vulnerability analysis activities may be performed with Naabu. Typical usage scenarios include:
- Network Mapping: The network topology may be mapped using Naabu, and each host’s open ports and services can be found.
- Vulnerability Assessment: Naabu may be used to find security holes in a variety of network services, including HTTP and FTP servers.
- Web Application Fingerprinting: Naabu may be used to identify the version and kind of web server being used, as well as to fingerprint online applications.
- Penetration Testing: Naabu is a tool that may be used in penetration testing to find possible weak points and attack routes.
Installing Naabu
The prerequisite for the Naabu tool are:
- Go Compiler
- libpcap-dev package
sudo apt-get install -y libpcap-dev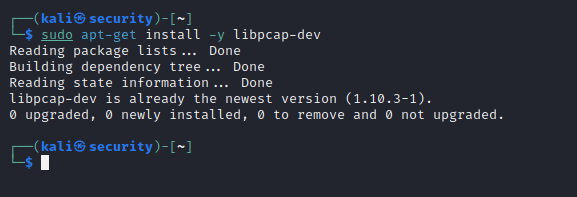
This tool can run in any Linux distribution such as Parrot Security OS, Kali Linux or Ubuntu.
Follow the steps to install the tool:
- Go to the GitHub page of the tool.
- Open terminal and type the command shown below.
go install -v github.com/projectdiscovery/naabu/v2/cmd/naabu@latest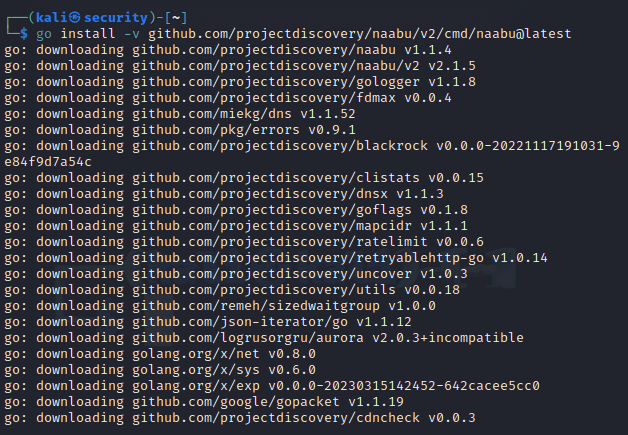
- Now, go to the location where naabu is installed. Check if the tool is installed or not by the ls command.
cd go/bin/
ls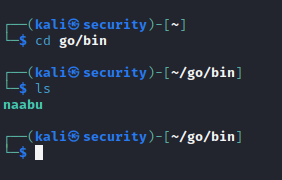
- Move naabu to the bin directory inside the file system.
sudo mv naabu /usr/bin/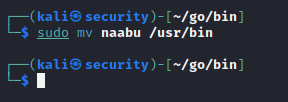
By moving it to the bin folder, the user can use the tool anywhere without specifying the tool’s location.
Running Naabu
To check this tool, we will use vulnhub.com.
- Normal run with the host-only.
naabu -host vulnhub.com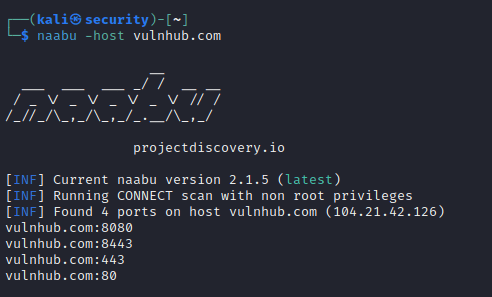
- Include port scan on the host
naabu -p 80,443 -host vulnhub.comNaabu uses Nmap for port scanning. It easily supports the in-built port list below:
| Flag | Description |
|---|---|
| -top-ports 100 | Top 100 port scanning |
| -top-ports 1000 | Top 1000 port scanning |
| -p – | Scan all ports from 1 to 65535 |
- Exclude specific ports
naabu -p - -exclude-ports 80,443- Run list of hosts & sace in JSON format
naabu -list hosts.txt -json- ASN Enumeration
echo AS13335 | naabu -p 80,443Integration with httpx
httpx is a fast, multi-purpose HTTP tool that checks status codes, titles, TLS info, etc. By integrating both tools, naabu and httpx, the active URLs will be shortlisted from the inactive ones.
echo vulnhub.com | naabu -p - | httpx -status-codeIntegration with Nmap
Naabu integrates smoothly with Nmap to provide in-depth port and service scanning after identifying live hosts. This hybrid approach balances Naabu’s speed with Nmap’s detail.
echo vulnhub.com | naabu -nmap-cli 'nmap -sV -oX nmap-output'IPv4 and IPv6 Use
This tool supports both IPv4 and IPv6 built-in to enable broad network scanning capabilities.
- IPv4
- Default mode – Naabu scans IPv4 addresses by default.
- Input formats – Accepts single IPs, IP ranges (eg, 192.168.1.1 – 255), and CIDR notation (eg, 192.168.0.0/24).
- Speed – High-performance scanning using raw sockets or SYN packets for fast port discovery.
- Use Case – Ideal for internal networks, public IP sweeps, and asset discovery.
- IPv6
- IPv6 Support – It is available by specifying the
-ip-version 6flag. - Targeting – Can scan single IPv6 addresses or ranges.
- Compatibility – It supports network and host system scanning.
Note – IPv6 scanning is slower and more complex due to the wide range of IPs.
- Scan both version of IPs
echo vulnhub.com | naabu -iv 4,6 -sa -silentHost Discovery
Host discovery in Naabu is a key feature that helps identify live hosts before conducting port scans and optimizes time and resources. Naabu uses ICMP, TCP, and UDP searches to detect if a host is up. It can be enabled or customized host discovery using -wn flag. To perform only host discovery, there is a flag -sn.
Options to perform host discovery.
| Option | Flag |
|---|---|
| ARP ping | -arp |
| TCP SYN ping | -ps 80 |
| TCP ACK ping | -pa 443 |
| ICMP echo ping | -pe |
| ICMP timestamp ping | -pp |
| ICMP address mask ping | -pm |
| IPv6 neighbor discovery | -nd |
naabu -host vulnhub.com -pingConfiguration File
Naabu supports using a configuration file to simplify and manage complex scans. This prevents from passing multiple flags on the command line every time runs.
The default config file path is: ~/.config/naabu/config.yaml
rate: 10000
retries: 2
timeout: 1000
ping: true
nmap: false
verify: true
exclude-cdn: true
ports: "80,443,8080"
interface: eth0Example of config.yaml
| Key | Description |
|---|---|
| rate | Packets per second (default is 1000) |
| retries | Number of retries for failed probes |
| timeout | Timeout in milliseconds |
| ping | Enable ICMP ping probes for host discovery |
| verify | Validate discovered open ports |
| exclude-cdn | Skip scanning known CDN IPs |
| nmap | Enable Nmap for service detection |
| interface | Specify a network interface to use |
| ports | Define ports to scan (range or list) |
naabu -list targets.txt -config ~/configs/naabu_custom.yamlConclusion
For network reconnaissance and vulnerability analysis, Naabu is a helpful tool. It is a versatile and effective tool for network scanning because of its modular architecture, adjustable scanning parameters, and detailed reporting. Network mapping, vulnerability analysis, web application fingerprinting, and penetration testing are just a few of the use cases for Naabu. Naabu is a quick, portable, and adaptable network scanner that you may use.


