Volatility 3 is a robust open-source memory forensics framework written in Python. Built from the ground up to replace its predecessor, Volatility2, it takes advantage of modern Python language practices and modular architecture. This article breaks down its internal architecture, explaining its core components, the role of plugins, and how its design benefits both analysts and developers.
Architecture Volatility 3 Overview
At its core, Architecture Volatility3 is built on a clean, object-oriented design that separates concerns into discrete components. This modularity is one of the main architectural improvements over Volatility2. The system is structured around three primary building blocks:
1. Framework Core includes base abstractions, interfaces, and standard utilities.
2. Plugins are standalone scripts that perform specific analysis tasks using the core APIs.
3. Layers and Contexts represent memory translation and address space abstraction.
All components interact through well-defined interfaces, allowing developers to extend or modify functionality without breaking the system.
Understanding Layers, Contexts, and Objects
Volatility3 introduces a layered memory model that is significantly more refined than Volatility2.
Below are the critical components:
- Memory Layer
- Contexts
- Templates and Objects
- Symbol Tables
Memory Layer
Memory in a computer is like a big warehouse full of storage boxes. Each box has an address, and early computers used to go straight to a box when they needed something — direct and straightforward. But as memory grew increasingly complex, that approach didn’t scale well. Modern systems break memory into fixed-size blocks called pages to manage things better. This setup helps keep things organized and easier to handle.
Instead of talking directly to physical memory, programs now use virtual addresses. The system has a sort of address book — a memory map — that translates these virtual addresses into the actual physical locations in memory. So, when a program asks for data at a certain virtual address, the processor checks the map and redirects the request to the right spot in physical memory.
Volatility (a memory forensics tool) knows how to work with these different memory layers — as long as it can find that map. At the start of an analysis, Volatility usually looks for the kernel’s memory map. It builds a virtual view of its memory so it knows where everything lives. Things get a little more complicated because each running process typically has its own memory map, even if parts of the operating system are shared. That means two programs could technically use the same virtual address. Still, those addresses could point to entirely different places — or even the same physical memory if they’re sharing data.
If you want to translate an address in Volatility, you can use the layer.mapping() function. Give it the offset (the address you’re interested in), the length of data you want, and whether it should ignore errors. It will return a list of “chunks” — pieces of successfully mapped data — showing where they came from and where they landed in physical memory. If something can’t be mapped and errors aren’t ignored, it’ll throw an error to let you know.
Contexts
A context is a container that holds all the necessary components for analysis. It manages the layers, plugins, and other metadata. It acts as the orchestrator, ensuring that plugins have access to the right memory views and data objects.
Templates and Objects
Once we can translate virtual memory addresses (the ones programs use) into actual locations in memory, we can start digging into memory to extract objects. To do this, we use something called a Template. Think of a Template like a blueprint — it tells us everything about how an object is laid out in memory: how big it is, what fields it has, where those fields are located, and what kind of data they might hold. But it doesn’t actually contain any real data — just the structure.
Using that Template and a specific memory location (an offset), we can then create an Object. In Volatility 3, this means reading the actual data from memory once and using it to build the object. After it’s built, Volatility doesn’t go back to memory to recheck it. The object holds onto its data, and we can inspect its fields, including following any pointers to related objects, making exploring complex structures easier.
A quick side note — Volatility 2 worked differently. It would keep re-reading memory each time you looked at something, which made it more suitable for live memory analysis but slower for typical static analysis (like examining a memory dump). Volatility 3 is designed for static memory, so you must rebuild the object yourself if the data changes. Also, Volatility 3 uses real Python types like integers and floats, which behave more predictably than the “proxy” types Volatility 2 used (those could get a bit quirky, especially during type checking).
Symbol Tables
Most compiled programs have a built-in understanding of their templates, which define how data is structured in memory. These templates are tied to something called symbols. Think of a symbol as a combination of an address and a type definition — it can point to where something is in memory and explain what that something is. During compilation, developers or debugging tools often create symbol lookup tables that map out this information to make it easier to explore or debug the program later.
In Volatility 3, this symbol information is organized using a SymbolTable, and you can group multiple symbol tables into a SymbolSpace. These SymbolSpaces are managed inside a Context, but knowing that each context can only hold one symbol space at a time is essential. Inside that symbol space, however, you can add as many symbol tables as you need — like putting multiple maps into one atlas.
Volatility 3 follows a standard way of naming symbols using the format module!symbol. It pulls this information from a JSON file, which acts like a translator between various symbol formats —whether Windows PDBs, Linux DWARF files, or others — and Volatility’s own Python-based format.
There are a few key differences if you’re coming from Volatility 2. What Volatility 3 calls a SymbolSpace was known as a profile in Volatility 2. But profiles had limitations — they couldn’t tell symbols from different modules apart, and dealing with 32-bit programs running under Wow64 on Windows was tricky. All the symbols were lumped into a single space, which could cause naming conflicts. Also, Volatility 2 used a format called vtypes, which meant defining symbols directly in Python code. This made it harder to share or reuse symbol info in other tools.
The Role of Plugins in the Ecosystem
Plugins are very important for Volatility3’s user experience. Each plugin is a standalone Python class that sticks to a specific interface defined by the framework. This class typically overrides a `run` method, where the analysis logic is implemented.
Plugins operate within the framework’s context, using layers, objects, and symbol tables to perform their work. Plugins are easy to write and maintain since they rely on stable, well-defined APIs.
Volatility 3 also ships with numerous built-in plugins for analyzing different operating systems, including Windows, Linux, and macOS. These plugins can be extended or used as references for creating custom analyses.
The Plugin Engine
The plugin engine in Volatility3 is responsible for discovering, loading, and running plugins.
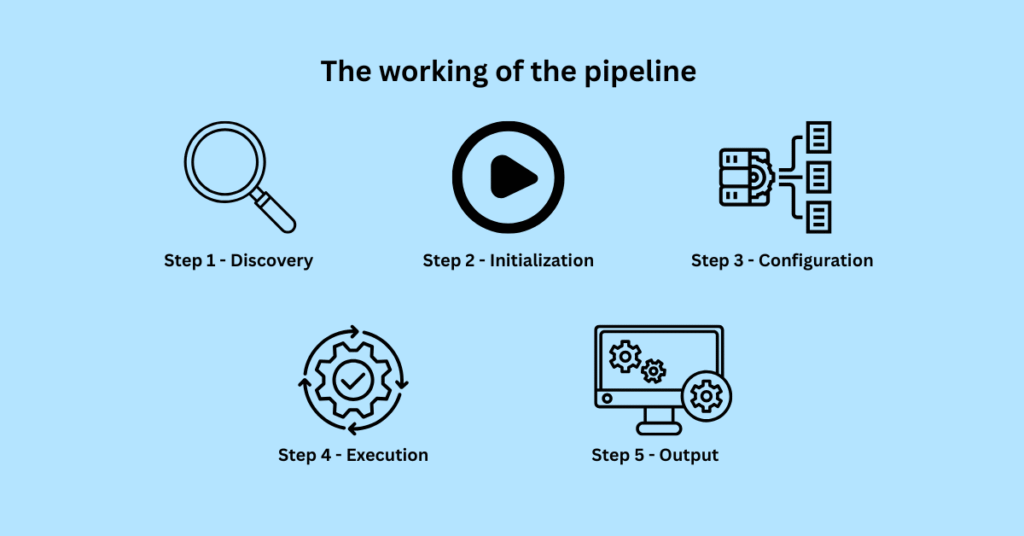
Below is the working of the pipeline:
1. Discovery: The framework scans for available plugin classes by inspecting specific Python modules.
2. Initialization: When a plugin is selected, the framework instantiates it within the active context.
3. Configuration: Input arguments are passed into the plugin, often using the framework’s argument parser.
4. Execution: The plugin’s `run` method is executed. It can access layers, perform address translations, and parse objects using symbol tables.
5. Output: Results are returned in a structured format (typically as `TreeGrid` objects) and rendered to stdout, JSON, or other formats.
This clean separation from input to output ensures reliability and facilitates automation in larger analysis workflows.
Benefits of the Modular Architecture
Volatility 3’s modular design is not just an academic improvement; it offers real benefits:
Ease of Extension: Developers can add new layers, plugins, or symbol tables without modifying core logic.
Testing: Individual modules are easier to unit test in isolation.
Cross-Platform Analysis: Support for multiple OSes (Windows, Linux, macOS) is cleaner and better organized.
Community Contributions: A stable plugin interface encourages community development.
Performance: Layer stacking allows optimizations like caching, lazy evaluation, and memory-mapped I/O.
Conclusion
Volatility 3 isn’t just a new version – it’s a complete architectural overhaul that brings memory forensics into a more modern and maintainable space. A modular, object-oriented foundation built in Python empowers developers and analysts to perform powerful, flexible investigations with less friction. From its layered memory model to its streamlined plugin system, Volatility 3 sets a new standard for what a forensic framework should be.


