Introduction
Do you want to become a penetration tester? But don’t know what a penetration tester is or how it’s differentiated by type or other approaches. Let’s dive into penetration testing in brief.
Penetration testing is one of the fastest-growing fields in cybersecurity. It is a very vast domain.
As black-hat hackers advance in skill and knowledge, it is the responsibility of organisations to ensure their cybersecurity systems can withstand attacks.
Pen-testing is one of the essential tools businesses can use to defend themselves.
A cybersecurity expert uses the same tactics as a black hat hacker to access your IT systems during penetration testing.
They employ every means a criminal could use, including password cracking, malware, and even social engineering.
Another name for penetration testing is pen-testing. Penetration testers are also known as pen testers.
Six Reasons You Need to Invest in Pen Testing:
- Pen testers expose an organisation’s weakness before real evil hackers do.
- It can show which areas of security require investment.
- It gives you an outsider’s perspective on your security.
- It will help you to save the organisation money.
- It represents a real-world cyber-attack situation.
- It will help you comply with the General Data Protection Regulation (GDPR) and other cybersecurity frameworks.
What is penetration testing?
A penetration test assesses the security of an information system by performing attacks, identifying system vulnerabilities, and recommending security fixes.
Some people think that pen testing and vulnerability testing are the same. But the fact is, both of them are very different in the real world.
Vulnerability testing includes automated scanners that quickly identify the most common vulnerabilities. Pen-testing takes a long time because it involves logical flaws that automated tools cannot detect, as well as a manual exploitation phase for discovered vulnerabilities.
A more precise, time-tested security audit method allows the full impact of any flaw to be measured.
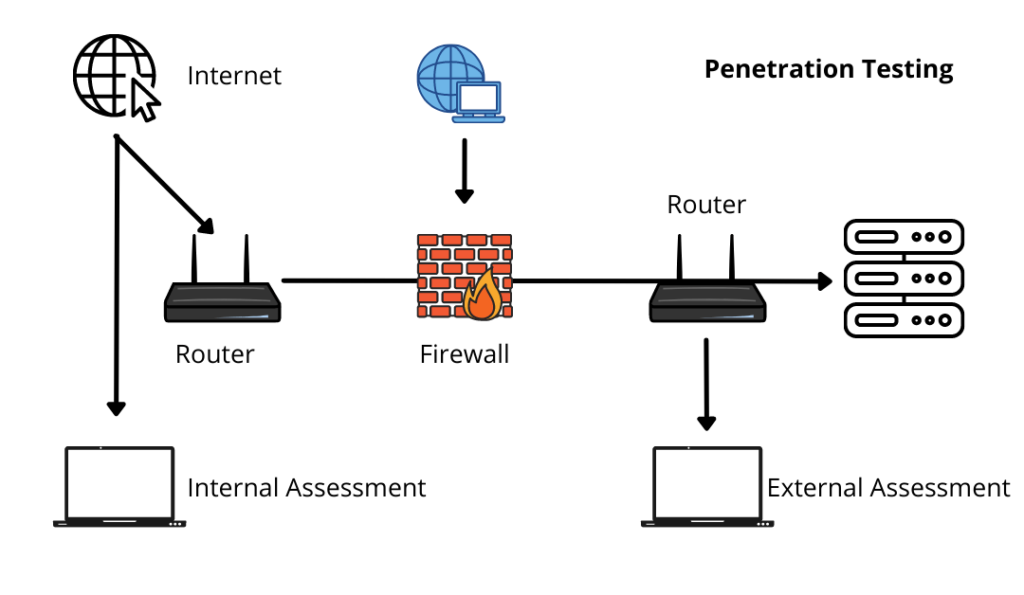
What is the fundamental goal?
In recent years, organisations have widely adopted pen testing as a security practice.
Pen testing is particularly appropriate for industries that store and access sensitive or private information, such as organisations, banks, or healthcare providers.
A pen test’s primary goal is to disclose vulnerabilities or exploit weaknesses. If they found any vulnerability, they have to report it to fix it. It helps the organisation stay safe from external attackers.
It is essential to highlight that the primary purpose of a pen test is often tied to a broader business objective.
The security objectives of a software company may differ depending on the organisation’s plan and strategy.
For instance, application pen-testing recognises vulnerabilities in code that might be powerless against an assault. Following that, developers work to implement fixes to update the codebase.
Finally, the types of pen-testing performed are determined by the business goals.
What are the different approaches?
The approach to penetration testing and the project’s scope depend on the information provided to the pen tester.
The organisation decides how much information to give to the pen tester.
The different approaches to pen-testing include:
- Black Box
- White Box
- Gray Box
Black Box Testing
Black Box Pen-testing is also known as External Penetration Testing.
Well, why is it called external? This approach is called external because the tester has little to no information about an organisation’s IT infrastructure.
In this method, the pen tester should think like an outside attacker (a black-hat hacker) and help the organisation identify unknown or unthinkable vulnerabilities.
Black box tests have some drawbacks:
- Limited knowledge makes it easy to miss deeper vulnerabilities that require internal knowledge.
- Pen testing an application from scratch takes a lot of time and energy.
- False negatives may occur between tests.
- It doesn’t measure how internal defences behave; it only measures the external surface.
White Box Testing
Internal Pen-testing, Clear Box Testing, and Glass Box Testing are other names for White Box approach.
The organisation will provide the tester with in-depth information about its IT infrastructure and access to its source code, depending on the scope of the attack.
What is a scope? A scope is a list of targets that the tester can test or not.
White box tests have some drawbacks:
- The organisation decides the level of access, but sometimes loses focus on real-world attack paths.
- Reporting takes time because teams must share internal documentation and architecture details.
- The results can feel unrealistic because attackers don’t have full access to source code or configuration files.
Grey Box Testing
The grey box approach is a mix of white and black-box approaches.
In this, the pen tester has only limited knowledge of or access to an internal network or a application. The rest of the information about the application, testers have to find it by themselves.
A pen tester may be granted user privileges on a host and instructed to escalate their privileges to a website admin. They could also request access to software code and system architecture diagrams.
Reporting from a grey-box penetration test provides a more focused, efficient assessment of your network’s security.
For example, rather than investing time in the “trial and error” approach, pen testers running a grey-box penetration test can survey network graphs to identify the most dangerous areas.
A pentester can recommend appropriate countermeasures to address the gaps.
Which approach is better?
Let the organisation decide based on its strategy, goals, and desired outcome. Different approach covers the purpose differently.
In the end, no matter which approach you take to safeguard your organisation, the only thing that matters is achieving the primary goal.
Types Of Penetration Testing
Each penetration test requires specific information, methodology, and tools and is aligned with a particular objective.
To achieve the organisation’s purposes, it is also necessary to develop an awareness of the different cyberattacks targeting its employees. It will help them implement secure code development to detect vulnerabilities in software code in real time or to meet regulatory or compliance requirements.
The different kinds of testing include:
- Network Penetration Testing
- Web Application Penetration Testing
- Client-Side Penetration Testing
- Wireless Penetration Testing
- Social Engineering
- Physical Penetration Testing
Network Penetration Testing
Network testing simulates the steps hackers would take to target a corporate network, its apps, websites, and devices.
This model seeks to detect security vulnerabilities early on before hackers can find and exploit them.
These tests, when performed correctly, go beyond simply preventing bad actors from gaining unauthorised access to an organisation’s network and data.
It helps generate real-world conditions to show corporations how effectively their current security systems would perform in confronting full-scale cyberattacks.
Network penetration tests are carried out to protect your organisation from common network-based attacks, such as:
- Firewall Misconfiguration And Firewall
- Bypass IPS/IDS Evasion Attacks
- Router Attacks
- DNS Level Attacks, Zone Transfer Attacks
- Switching Or Routing-Based Attacks
- SSH Attacks
- Proxy Server Attacks
- Unnecessary Open Ports Attacks
- Database Attacks
- Man In The Middle (MITM) Attacks
- FTP/SMTP-Based Attacks
Since a network delivers mission-critical services to an organisation, internal and external network testing should be performed annually. Pen testing provides your organisation with sufficient protection against these attack vectors.
Web Application Penetration Testing
Web Application testing aims to identify vulnerabilities or security threats in web-based applications.
Various techniques and attacks are used to break into a web application.
A web application test’s standard scope covers web-based applications, browsers, and associated components such as JSP, Silverlight, Servlet, EJB, and Applets.
Because these tests are considerably more thorough and focused, they are considered more complicated. Endpoints of any web-based application that regularly interact with the user must be identified to perform a successful test.
From planning the test through execution to generating a usable report, this involves effort and time.
Testing methodologies for web testing are constantly evolving as the number of daily threats originating from web apps increases.
A primary objective of a web application penetration test is to identify security vulnerabilities across applications, including databases, source code, and back-end networks.
It also helps by prioritising the discovered flaws or vulnerabilities and suggesting potential mitigation solutions.
It is considered excellent practice in software development to continually enhance the codebase. The phrase “deploying secure and agile code” is frequently used to characterise this technique.
Client-Side Penetration Testing
Client-side testing is performed to identify vulnerabilities or security flaws in client-side applications.
These might include Putty, email clients, web browsers (such as Chrome, Firefox, Safari, and others), Macromedia Flash, etc.
Client-side testing is carried out to detect unavoidable cyberattacks, such as:
- Cross-Site Scripting Attacks
- Clickjacking Attacks
- Cross-Origin Resource Sharing (CORS)
- Form Hijacking
- HTML Injection
- Open Redirection
- Malware Infection
Wireless Penetration Testing
Wireless testing involves identifying and analysing the connections between all devices linked to the organisation’s Wi-Fi. These gadgets include laptops, tablets, smartphones, and other Internet of Things (IoT) devices.
Wireless testing was carried out on-site since the pen tester must be within range of the wireless signal to access it. Alternatively, a NUC and Wi-Fi Pineapple (optional) are put on-site to run the test remotely.
Wireless communications are a service that runs anonymously and allows data to move in and out of the network. As a result, any flaws in this wireless network, such as illegal access or data leakage, must be addressed.
Important points to be considered:
- Pentester should identify all access issues.
- Avoid using poor encryption methods.
- The data flowing in or out of the system is encrypted.
- Place monitoring systems to identify unauthorised users.
- All wireless access points should use the WPA protocol.
Social Engineering Penetration Testing
During social engineering testing, a malicious person attempts to convince or deceive people into disclosing sensitive information, such as a login and password.
Below is the list of different attacks categorised in social engineering:
- Phishing Attacks
- Vishing Attacks
- Smishing
- Tailgating
- Imposters (i.e., Fellow Employees, External Vendors, or Contractors)
- Name Dropping
- Pre-texting
- Dumpster Diving
- Eavesdropping
- Gifts
According to recent data, social engineering is used in 98% of all cyber attacks. Internal employees are among the most dangerous threats to a network’s security, and the scams are profitable.
Social engineering testing and awareness campaigns are among the most effective attack-mitigation techniques.
Physical Penetration Testing
Physical testing simulates a real-world threat. A tester attempts to breach physical boundaries to access an organisation’s infrastructure, facility, systems, or individuals.
Suppose an attacker gains physical access to the server room of any organisation. In that case, they can take complete control of your network. Most organisations underestimate the situation.
This impact could have on your organisation, consumers, and business partners.
The significant advantage of a physical penetration test is that it exposes gaps and vulnerabilities in physical controls (locks, barriers, cameras, or sensors), allowing problems to be fixed immediately. By detecting these flaws, suitable solutions are implemented to enhance the physical security posture.
Penetration Testing Tools
The most crucial element of performing penetration testing is choosing the correct tool for the job based on the challenges you’re experiencing. Some of the popular tools are:
Conclusion
Penetration testing and vulnerability testing are distinct testing methods. A penetration test aims to expose and exploit flaws in an organisation’s IT infrastructure. Pen testing is beneficial in areas where sensitive or private information is stored and accessed, such as banks or healthcare providers. Each penetration test demands specific information, methodology, and tools and is focused on a particular goal.








