Subdomain enumeration is important in cybersecurity because it helps detect security flaws inside a target domain. Knock Subdomain Scan, a Python-based application for quick and efficient subdomain enumeration, is one of the best tools for the job.
This article explores Knock Subdomain Scan, its features, installation process, usage, and best practices for penetration testers and ethical hackers.
What is Knock Subdomain Scan?
Knock Subdomain Scan is an open-source tool written in Python that automates the process of discovering subdomains. It helps security professionals uncover potential attack surfaces by identifying subdomains associated with a target domain.
Key Features
- Fast and efficient subdomain enumeration
- Python-based and lightweight
- Uses a wordlist-based attack
- Supports wildcard DNS resolution
- Open-source and regularly updated
Why is Subdomain Enumeration Important?
Subdomain enumeration is critical for:
- Identifying additional attack vectors
- Discovering hidden services or applications
- Enhancing penetration testing efficiency
- Unveiling potential security misconfigurations
- Assisting bug bounty hunters in finding vulnerabilities
Installing Knock Subdomain Scan
Knock Subdomain Scan is compatible with Linux and Mac OS and requires Python to run.
Prerequisites
- Python 3.x
- Git installed
Installation Steps
- Open your terminal and clone the repository:
git clone https://github.com/guelfoweb/knock.git
- Navigate to the Knock directory:
cd knock- First, set up virtual environment:
python3 -m venv myenv
source myenv/bin/activate
- Install the dependencies:
pip install -r requirements.txt
- Verify the installation by running:
python3 knockpy.py -h
How to Use Knock Subdomain Scan?
After installing the tool, you can start scanning for subdomains.
Basic Subdomain Enumeration
To enumerate subdomains of a target domain, use:
python3 knockpy.py example.com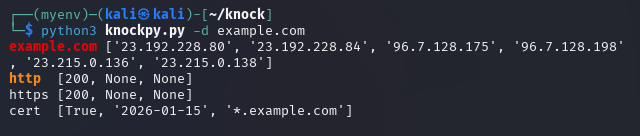
This command will scan example.com for subdomains using the built-in wordlist.
Using a Custom Wordlist
For a more thorough scan, you can specify a custom wordlist:
python3 knockpy.py example.com --wordlist /path/to/wordlist.txtSaving Results to a File
To save scan results in JSON format:
python3 knockpy.py example.com -o results.jsonChecking Wildcard Subdomains
Knock also detects wildcard DNS configurations, helping identify false positives:
python3 knockpy.py example.com --wildcardBest Practices for Subdomain Enumeration
- Use multiple tools: Combine Knock with other enumeration tools like Sublist3r and Amass for comprehensive results.
- Leverage large wordlists: Use an extensive wordlist like SecLists for better coverage.
- Perform periodic scans: Regularly check for new subdomains to identify emerging threats.
- Analyze wildcard DNS: Avoid false positives by verifying wildcard subdomains.
- Respect legal guidelines: Always seek permission before scanning any domain to avoid legal consequences.
Alternatives to Knock Subdomain Scan
While Knock is powerful, here are some alternative tools:
- Sublist3r – Uses OSINT sources for enumeration.
- Amass – Advanced reconnaissance tool with active and passive scanning.
- Assetfinder – Fast subdomain discovery via APIs.
Conclusion
Knock Subdomain Scan is a quick, efficient, easy-to-use tool for ethical hackers, penetration testers, and bug bounty hunters. Its ease of use and open-source availability make it a valuable cybersecurity reconnaissance tool. Incorporating Knock into your pen-testing workflow might improve domain reconnaissance and security posture.


