With the ever-evolving landscape of cybersecurity, penetration testers and security researchers need effective tools to help them identify possible vulnerabilities in web applications. Cariddi is one tool that helps simplify the process of finding endpoints from JavaScript files and other sources.
This article explores Cariddi’s features, installation, usage, and benefits, making it an essential resource for cybersecurity professionals.
What is Cariddi?
Cariddi is an open-source endpoint finder tool that assists security professionals in extracting sensitive endpoints from web applications. It is an excellent tool for reconnaissance and vulnerability assessment since it is very good at parsing HTML, evaluating JavaScript files, and accessing API endpoints.
Key Features
This tool stands out due to its impressive feature set, which includes:
- JavaScript File Parsing: Extracts endpoints from JavaScript files, allowing security professionals to identify API calls.
- URL and Endpoint Extraction: Finds URLs, API keys, and sensitive endpoints embedded in HTML, JavaScript, and other files.
- Recursive Crawling: Can recursively analyze websites to discover hidden endpoints.
- User-Agent Customization: Enables users to modify request headers for better stealth.
- Fast and Efficient: Built with performance in mind, It quickly scans and processes web content.
- Integration with Other Tools: Works seamlessly with other penetration testing tools like Burp Suite and OWASP ZAP.
Installation Guide
Installing Cariddi is easy. Follow these steps:
Prerequisites
Before installing the tool, ensure you have the following dependencies:
- Go (Golang) installed on your system.
Installation Steps:
- Clone the Cariddi repository from GitHub:
git clone https://github.com/edoardottt/cariddi.git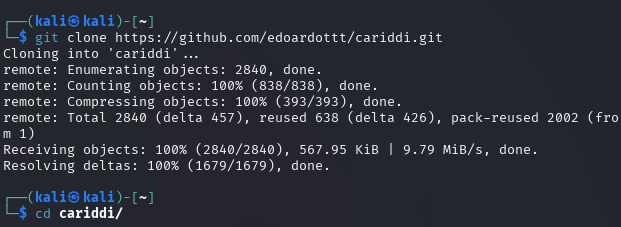
- Navigate to the tool’s directory:
cd cariddi/- Build the tool using Go:
go get ./...
make linux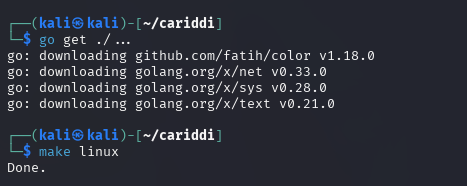
- Run the tool:
echo testphp.vulnweb.com | cariddi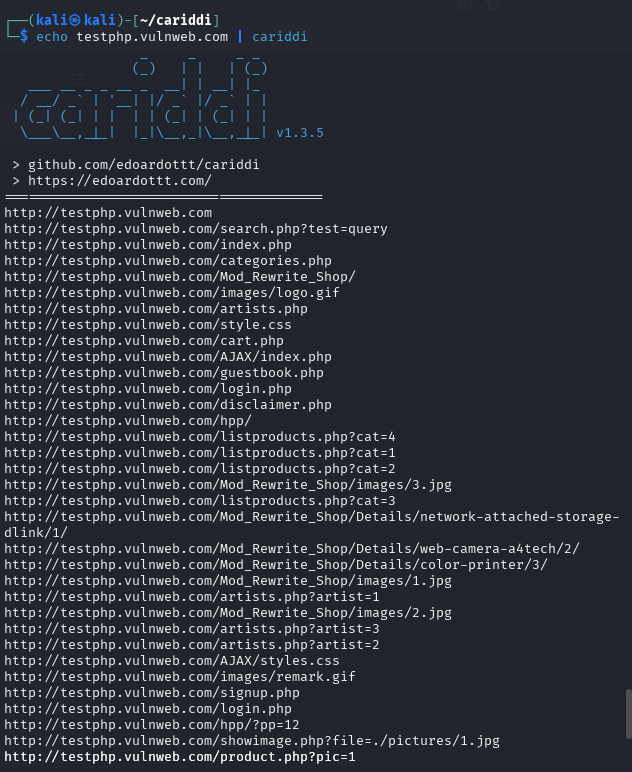
How to Use Cariddi?
This tool offers multiple options for scanning web applications. Here are a few common use cases:
- Extract Endpoints from a JavaScript File
To scan a JavaScript file for endpoints, use:
cariddi -u https://example.com/script.js- Scan an Entire Website
To recursively analyze a website and extract endpoints, use:
cariddi -d https://example.com- Customize User-Agent
To specify a custom User-Agent string, use:
cariddi -u https://example.com -A "Mozilla/5.0 (Windows NT 10.0; Win64; x64)"- Save Output to a File
To save extracted endpoints to a file, use:
cariddi -u https://example.com -o output.txtUse Cases in Cybersecurity
This tool serves multiple purposes in cybersecurity and ethical hacking, including:
- Bug Bounty Hunting: Helps researchers discover API endpoints and sensitive data exposures.
- Penetration Testing: Assists in identifying hidden API calls for security testing.
- Reconnaissance & OSINT: Extracts valuable data for intelligence gathering and target enumeration.
- Web Application Security Audits: Facilitates security assessments by revealing potential vulnerabilities.
Advantages
- There is no licensing fees, making it accessible for all as it is open-source.
- It uses minimal resource consumption while delivering high performance.
- It works well with existing security tools and scripts.
- Automating endpoint discovery, and reducing manual effort.
Potential Limitations
While this tool is strong, there are certain limitations:
- False Positives: Some collected endpoints may not represent genuine vulnerabilities.
- Limited Language Support: Works largely with JavaScript and HTML endpoints.
- Manual validation is required: Users must check the correctness of extracted data.
Summary
Cariddi is a necessary utility for security researchers, penetration testers, and bug bounty hunters who would be required to harvest endpoints from web applications with minimal effort. It is a valuable addition to any cybersecurity arsenal because of its long list of features, simplicity, and integration capabilities. Security professionals are able to complement their reconnaissance and vulnerability scanning activity using this tool , which will ultimately improve online applications’ security stance.


