The Cyber Kill Chain is a step-by-step process for identifying and stopping an attacker’s activity. Lockheed Martin created this framework in 2011. The steps of the Cyber Kill Chain illustrate the duration of advanced persistent threats (APTs) and the sequence of events that unfold.
Typically, these types of attacks operate a combination of malware, ransomware, Trojans, spoofing, and social engineering tactics to achieve their objectives.
Security teams currently utilize Cyber Kill Chain framework to map threats to specific phases, which enables them to prioritize defenses and identify vulnerabilities.
In this article, we outline the framework for each step and explain how it works within the organization.
The Function of the Cyber Kill Chain in Cybersecurity
Despite several vulnerabilities, the Cyber Kill Chain is an effective tool for helping firms establish their cybersecurity strategy. The Cyber Kill Chain paradigm requires enterprises to implement services and solutions that enable them to:
- Detect attackers at all stages of the threat lifecycle using threat intelligence approaches.
- Prevent access from unauthorized users.
- Protect sensitive data from being shared, stored, edited, exfiltrated, or encrypted by unauthorized users.
- Respond to attacks in real time.
- Stop the attacker’s lateral movement within the network.
How the Cyber Kill Chain Works?
The Cyber Kill Chain framework begins with gathering information and ends with distributing the data. This framework comprises seven different steps that work together. It helps to understand, analyze, and defend against cyber threats.
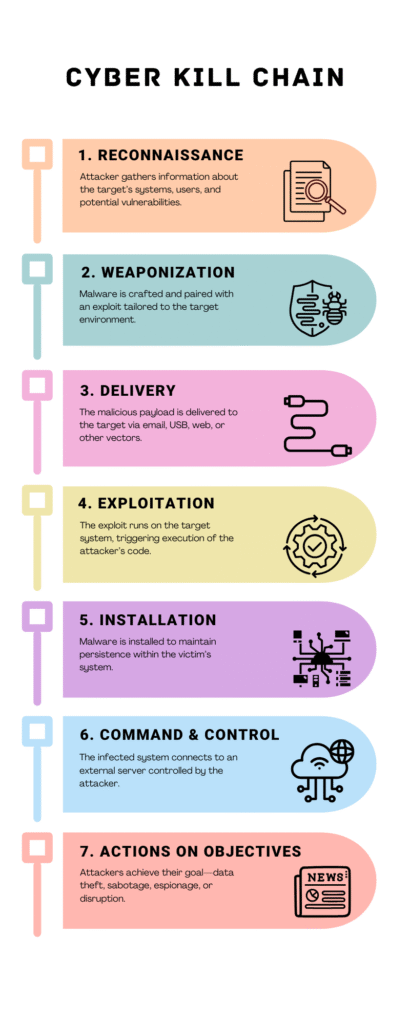
This illustration shows the step-by-step working of the framework.
Step 1 – Reconnaissance
Initially, the attacker begins to gather information through various tools, which is known as Reconnaissance. This step is very important in Cyber Kill Chain framework.
In this step, an attacker identifies a target and analyzes it to find vulnerabilities and weaknesses that can be exploited within the network.
Below is the list of information an attacker is looking for:
- Email addresses
- Login Credentials (username, password)
- Physical Locations
- Software Applications
- Operating System
In general, the more information the attacker can obtain during the Reconnaissance phase, the more complex and convincing the attack will be, increasing the probability of success.
For example, if an attacker wants to attack an organization. They will find information from LinkedIn (such as who is working and the organizational structure) and Hunter.io (to find work email addresses). After gathering all the information, they can conduct social engineering to gain access to the system.
Adversary Actions:
- Collect software and server version information.
- Identify publicly available data (e.g, social media, web archives).
- Find employee emails or internal details.
- Locate IP ranges and internet-connected devices.
- Detect vulnerabilities on accessible servers.
Defender Actions:
- Conduct external penetration testing to identify data exposure.
- Monitor threat intelligence for leaks.
- Avoid publicly sharing sensitive documents.
- Use firewalls and other security tools to monitor internet-accessible assets.
- Patch vulnerabilities promptly.
Step 2 – Weaponization
Weaponization is a step where an attacker creates a payload or malware to exploit a target, either by modifying existing malware or creating new malware.
Adversary Actions:
- Create malware or develop exploits.
- Design phishing emails with malicious content.
- Choose appropriate tools for the attack.
Defender Actions:
- Regularly audit systems for known vulnerabilities.
- Install patches promptly.
- Test and analyze known attack tools to detect usage.
Step 3 – Delivery
In the Delivery step, the attacker must launch the attack, but how will they do so? Here, they will determine the type of attack to use based on their intention.
They can use multiple ways:
- Email Attachments
- Phishing Links
- Malicious Macros in Office Docs
- Drive-by Downloads
- Fake Software Updates
- USB Drops
- Rogue Browser Extensions
- Fake Mobile Apps
- QR Code Phishing
The methods mentioned above are used to deliver malicious files or software to the target machine.
Adversary Actions:
- Send malicious links or files via email or social media.
- Upload malware to websites or target servers.
- Use physical methods, such as USB devices.
Defender Actions:
- Avoid interacting with unknown links or files and use sandbox environments.
- Scan email attachments with antivirus tools.
- Implement email security solutions.
- Train users on phishing awareness.
- Monitor server access and review logs.
Step 4 – Exploitation
This step of the Cyber Kill Chain leverages vulnerabilities discovered during reconnaissance to execute the malicious payload provided in the previous step. Once the system is successfully exploited, the attacker can gain full root access.
Understanding how exploitation fits into the Cyber Kill Chain enables defenders to anticipate these actions and adopt appropriate security measures to thwart the attacker’s advances.
Adversary Actions:
- Exploit hardware/software vulnerabilities.
- Execute malicious scripts or tools.
Defender Actions:
- Train staff to recognize suspicious files or requests.
- Monitor systems for anomalies and exploits.
- Install security updates promptly.
- Use Endpoint Detection and Response (EDR) tools.
- Conduct regular penetration testing and vulnerability scans to identify potential security risks.
Step 5 – Installation
Once an attacker is inside the system, they want a permanent way to stay in. For this, the attacker must install backdoor access on multiple systems, making it challenging to discover and recover.
If they successfully install a backdoor on multiple systems, they can return and continue their attack at any time.
Adversary Actions:
- Install malware or backdoors.
- Deploy web shells or schedule tasks for persistent access.
Defender Actions:
- Monitor network security continuously.
- Use EDR (Endpoint Detection and Response) tools to detect configuration changes.
- Restrict access to critical files and paths.
- Monitor processes for unauthorized activities.
- Enforce least privilege access policies.
Step 6 – Command and Control
Once the attacker establishes a command and control (C2) system. This enables them to administer and control infected computers, provide commands to malware, and exfiltrate data. Attackers must keep control of the compromised environment.
They utilize obfuscation techniques to conceal their tracks, as well as denial-of-service (DoS) tactics to divert the security team’s attention away from the primary objectives of the attack.
Adversary Actions:
- Configure C2 servers.
- Establish C2 communication with the victim’s system.
Defender Actions:
- Block known malicious IP addresses using firewall rules.
- Monitor network traffic for anomalies.
- Detect C2 tools and patterns.
Step 7 – Actions on Objectives
This is the final step in the Cyber Kill Chain. If an attacker reaches this stage, it means they have achieved their objectives, ranging from stealing sensitive information to disrupting business operations or demanding a ransom, which are their intended intentions. Attackers also declare what they did and how they did it.
Adversary Actions:
- Encrypt data (e.g., ransomware).
- Exfiltrate critical information.
- Escalate privileges for deeper access.
- Delete or manipulate system data.
Defender Actions:
- Monitor for network anomalies.
- Restrict external data transfer and monitor access to ensure security.
- Limit access to sensitive files and databases.
- Use Data Loss Prevention (DLP) tools.
- Detect unauthorized actions promptly.
Real-World Examples in Cyber Kill Chain
Now, we will discuss three real-world examples to understand how the Cyber Kill Chain really works.
1. Target Data Breach (2013)
- Reconnaissance: Attackers identified a third-party HVAC vendor with weak security as a means of gaining access to Target’s network.
- Weaponization: They created malware (a variant of BlackPOS) specifically designed to scrape memory from point-of-sale (POS) systems.
- Delivery: The malware was delivered through phishing emails sent to the HVAC vendor. Once the vendor’s credentials were compromised, attackers used Target’s vendor portal.
- Exploitation: They used the stolen credentials to log in and move laterally within Target’s network.
- Installation: POS malware was installed across the retail environment to capture credit card data in real-time.
- Command & Control (C2): Data was exfiltrated to attacker-controlled servers, often routed through compromised servers in other countries.
- Actions on Objectives: Credit and debit card info of 40 million customers was stolen, leading to financial fraud and major brand damage.
2. WannaCry Ransomware Attack (2017)
- Reconnaissance: WannaCry wasn’t a targeted attack, so this phase was automated. It scanned the internet for machines with SMBv1 enabled.
- Weaponization: The malware used the EternalBlue exploit (developed by the NSA and leaked by Shadow Brokers) to spread.
- Delivery: It was delivered as a worm—no phishing needed. If a machine had SMBv1 exposed, it got infected.
- Exploitation: Once in, the ransomware exploited unpatched Windows systems using EternalBlue and DoublePulsar.
- Installation: The ransomware component was dropped and executed on the target machine.
- Command & Control (C2): Minimal C2. It was more of a “fire and forget” model. The malware checked a kill-switch domain to see if it should stop spreading.
- Actions on Objectives: Encrypted files on over 200,000 machines in 150+ countries. NHS hospitals in the UK were badly hit. Bitcoin ransom was demanded.
3. SolarWinds Supply Chain Attack (2020)
- Reconnaissance: The attackers (likely APT29) studied SolarWinds’ internal build systems and update process for Orion software.
- Weaponization: They inserted a stealthy backdoor (SUNBURST) into legitimate Orion software updates.
- Delivery: The compromised updates were digitally signed and pushed to 18,000+ customers, including government and Fortune 500 organizations.
- Exploitation: Once installed, the backdoor lay dormant for weeks, then activated by contacting attacker-controlled domains.
- Installation: Attackers used SUNBURST to drop additional malware, gain credentials, and move laterally within networks.
- Command & Control (C2): SUNBURST communicated with attackers over DNS and HTTP, blending in with normal traffic to avoid detection.
- Actions on Objectives: Massive espionage operation. Attackers accessed sensitive data from U.S. government agencies, Microsoft, and others. It was stealthy and persistent.
Conclusion
Understanding the Cyber Kill Chain is not only for threat analysts; it is a realistic paradigm that can help everyone in cybersecurity understand how attackers think and behave.
By breaking out each stage of an attack, from early reconnaissance to ultimate data exfiltration, defenders can detect red flags sooner, stop attacks in progress, and protect systems before they are compromised.
Whether you’re developing a SOC strategy or simply enhancing incident response, mapping threats to the Kill Chain transforms conjecture into actionable steps.
Resources
- Cybersecurity Test Website Vulnerabilities: 10 Powerful Techniques to Boost Your Security
- Cyber Kill Chain, 2017
- Cyber Kill Chains: Strategies & Tactics
- Blue TryHackMe Walkthrough (upcoming)


