If you’re just getting started with ethical hacking or network troubleshooting, Nmap should be one of the first tools you master.
Nmap, or Network Mapper, is an open-source, very flexible application used by Linux systems and network administrators. It is frequently used for network exploration, security scanning, auditing, and discovering open ports on remote computers.0
Nmap can detect active hosts, operating systems, packet filters, and open ports on distant computers.
In this guide, we’ll walk through 30 practical Nmap commands that you can start using right away — with clear explanations so you understand what each one does.
Why 28 Basic Nmap Commands Matter?
- Covers Core Use Cases
These commands help you perform essential tasks like port scanning, service detection, OS fingerprinting, and vulnerability assessment — all with precision. - Balance of Power and Simplicity
The 28 commands give you powerful scanning capabilities without overwhelming complexity, making them perfect for beginners and pros alike. - Real-World Relevance
They reflect what security professionals and sysadmins actually use in daily recon, pen testing, and auditing tasks. - Faster, Smarter Scanning
Knowing these commands helps you optimize scans for speed, stealth, and accuracy, saving valuable time during engagements. - Builds Strong Foundation
Mastering these basics prepares you for more advanced Nmap usage (like custom NSE scripts or large network automation). - Flexible for Any Situation
Whether you’re scanning a single host, a subnet, or avoiding detection, these commands adapt to different scenarios.
Scan Specific Domain or an IP Address
nmap <target>This command scans the device at IP address 192.168.1.1 and shows which ports are open. It’s the simplest way to check if a host is up and running and to determine which services might be available.
You can also use any domain name instead of an IP address.
Use this when troubleshooting a device on your local network or when you want to safely start scanning a known host.
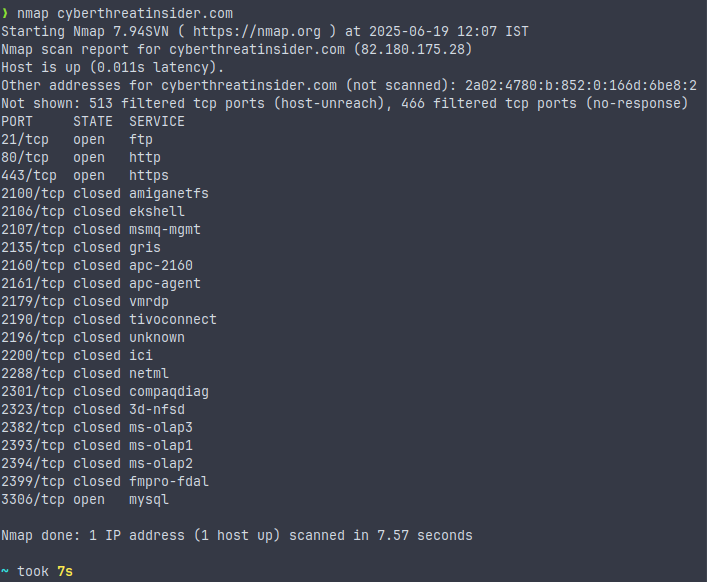
As you can see, all ports are listed after the scan, including those that are closed.
Scan Entire Subnet
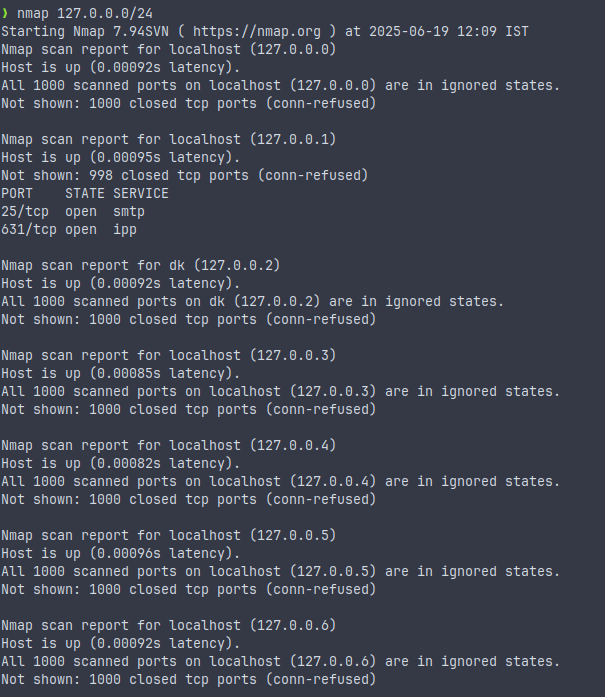
nmap 127.0.0.0/24This command scans all hosts available in the subnet associated with the specified IP Address. It will display all hosts that are up in the network range.
Use this when you are in a network but don’t know the IP address of the victim.
Scan specific port
nmap -p 80 <target>This command will scan only the specified port on the target. It’s a quick scan because it will exclude all other open ports.
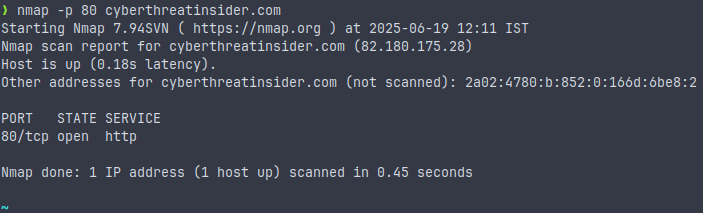
Use this command to check if the server hosts a website; you will quickly get the result. Or if you are targeting a specified port on the target.
Scan Port Range
nmap -p 1-1000 <target>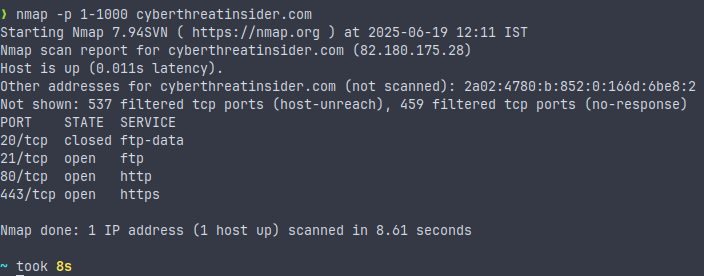
This command will scan the range of ports specified by you.
Scan Fast All Standard Ports
nmap -F <target>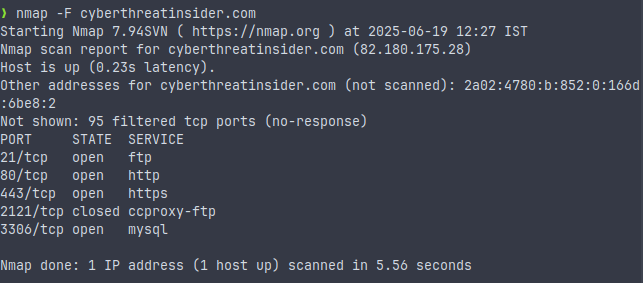
This command will scan fast and only a few default ports.
Scan all ports (all 65535 ports)
nmap -p- <target>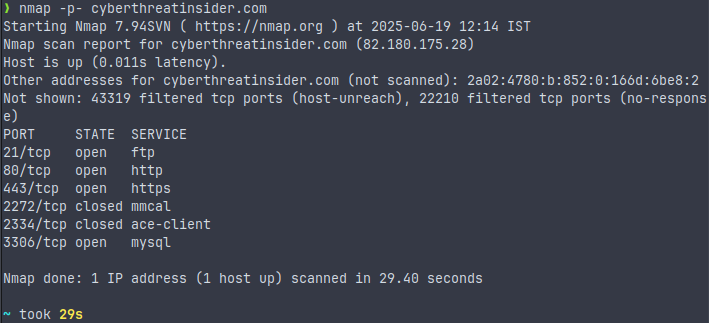
This command will scan all ports available on a server, i.e., 65535 ports. This process takes longer, as it scans all ports individually.
Service & Version Detection
nmap -sV <target>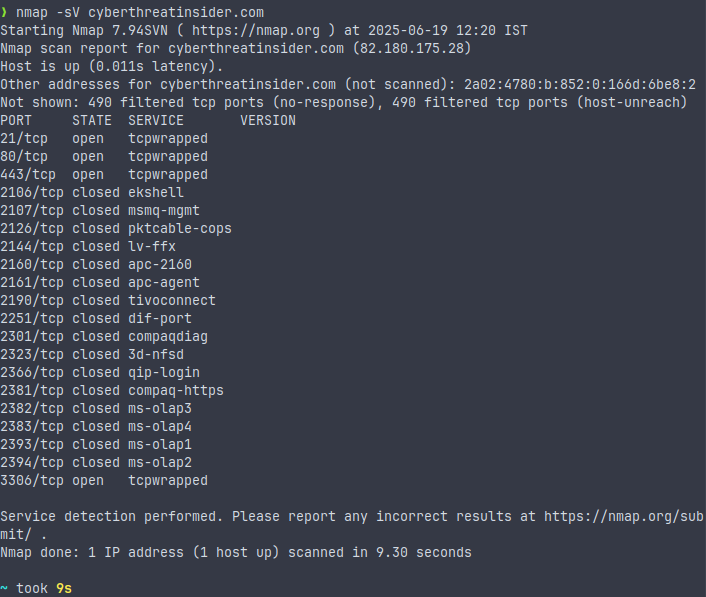
This command scans and detects the version of services running on different ports. This is useful for finding any outdated services running on the server.
Aggressive Scan
nmap -A <target>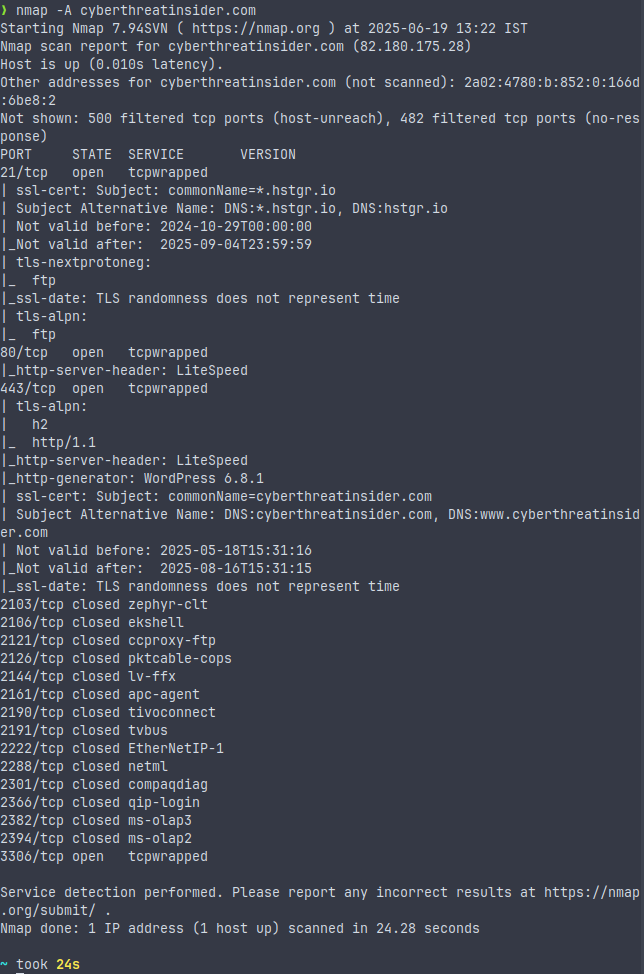
This command will detect the OS, version name, run the NSE default script, and perform a traceroute of the server. This is a very noisy and aggressive scan.
Detail About Versions
nmap --version-all <target>This command enables detailed version information and provides additional details.

OS Detection
sudo nmap -O <target>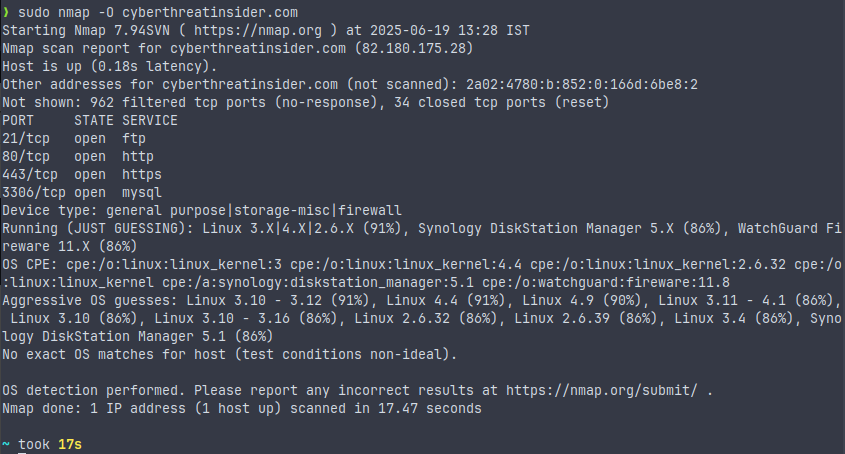
This command detects the operating system (OS) of the target. To run this command, you need root (sudo) privileges.
Aggressive OS Detection
sudo nmap -O --osscan-guess <target>
This command is more aggressive in finding the operating system (OS) of the target.
TCP SYN (Stealth) scan
sudo nmap -sS <target>The command will send a SYN packet (like starting a 3-way handshake) but doesn’t complete the connection. This is very stealthy, as the connection is not complete. This needs root privilege (sudo) as it sends raw packets.
UDP scan
sudo nmap -sU <target>This command is used to find UDP ports, such as port 53 and port 161, among others. It is slow, less reliable, and misses filtered ports.
TCP Null scan
sudo nmap -sN <target>This command sends TCP packets with no flags set. The purpose is to bypass firewalls or obscure operating system fingerprinting.
Xmas Scan
nmap -sX <target>This command sends a TCP packet with different flags set (FIN, URG, and PSH). It is very similar to a Null scan. It is limited in terms of stealthy.
FIN scan
nmap -sF <target>This command sends a TCP packet with only the FIN flag set. It is stealthy to a certain extent, as it doesn’t complete the handshake.
Normal Output
nmap -oN output.txt <target>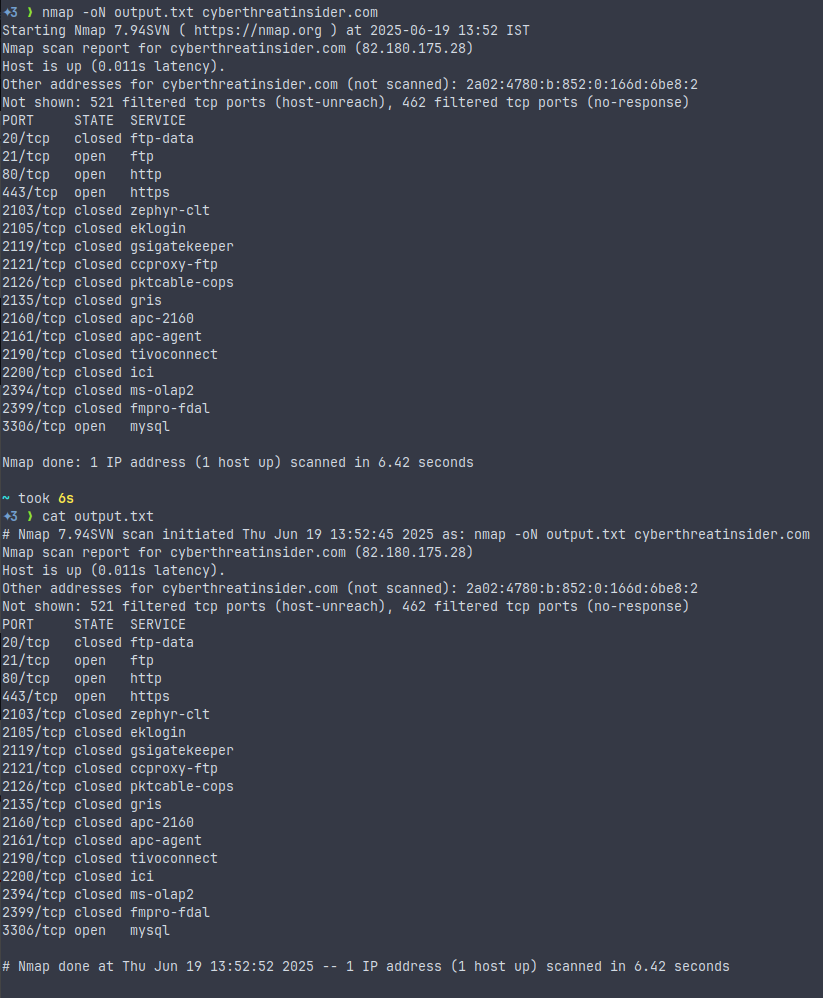
- Format: Human-readable (what you see in the terminal).
- Use case: Good for reviewing or sharing with people.
XML Output
nmap -oX output.xml <target>- Format: XML (structured markup).
- Use case: Ideal for parsing programmatically with tools, scripts, or other security platforms.
- Used by Tools like ndiff, xsltproc, and custom parsers.
- Note: You can convert XML to HTML using Nmap’s XSL stylesheet.
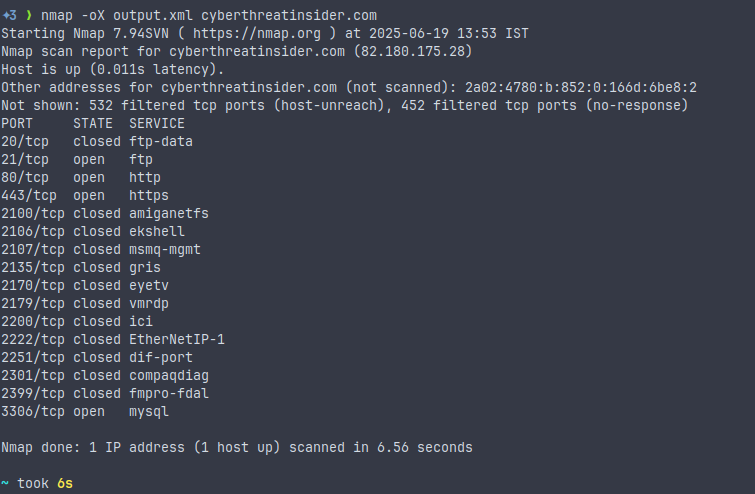
XML Output
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE nmaprun>
<?xml-stylesheet href="file:///usr/bin/../share/nmap/nmap.xsl" type="text/xsl"?>
<!-- Nmap 7.94SVN scan initiated Thu Jun 19 13:53:58 2025 as: nmap -oX output.xml cyberthreatinsider.com -->
<nmaprun scanner="nmap" args="nmap -oX output.xml cyberthreatinsider.com" start="1750337638" startstr="Thu Jun 19 13:53:58 2025" version="7.94SVN" xmloutputversion="1.05">
<scaninfo type="connect" protocol="tcp" numservices="1000" services="1,3-4,6-7,9,13,17,19-26,30,32-33,37,42-43,49,53,70,79-85,88-90,99-100,106,109-111,113,119,125,135,139,143-144,146,161,163,179,199,211-212,222,254-256,259,264,280,301,306,311,340,366,389,406-407,416-417,425,427,443-445,458,464-465,481,497,500,512-515,524,541,543-545,548,554-555,563,587,593,616-617,625,631,636,646,648,666-668,683,687,691,700,705,711,714,720,722,726,749,765,777,783,787,800-801,808,843,873,880,888,898,900-903,911-912,981,987,990,992-993,995,999-1002,1007,1009-1011,1021-1100,1102,1104-1108,1110-1114,1117,1119,1121-1124,1126,1130-1132,1137-1138,1141,1145,1147-1149,1151-1152,1154,1163-1166,1169,1174-1175,1183,1185-1187,1192,1198-1199,1201,1213,1216-1218,1233-1234,1236,1244,1247-1248,1259,1271-1272,1277,1287,1296,1300-1301,1309-1311,1322,1328,1334,1352,1417,1433-1434,1443,1455,1461,1494,1500-1501,1503,1521,1524,1533,1556,1580,1583,1594,1600,1641,1658,1666,1687-1688,1700,1717-1721,1723,1755,1761,1782-1783,1801,1805,1812,1839-1840,1862-1864,1875,1900,1914,1935,1947,1971-1972,1974,1984,1998-2010,2013,2020-2022,2030,2033-2035,2038,2040-2043,2045-2049,2065,2068,2099-2100,2103,2105-2107,2111,2119,2121,2126,2135,2144,2160-2161,2170,2179,2190-2191,2196,2200,2222,2251,2260,2288,2301,2323,2366,2381-2383,2393-2394,2399,2401,2492,2500,2522,2525,2557,2601-2602,2604-2605,2607-2608,2638,2701-2702,2710,2717-2718,2725,2800,2809,2811,2869,2875,2909-2910,2920,2967-2968,2998,3000-3001,3003,3005-3007,3011,3013,3017,3030-3031,3052,3071,3077,3128,3168,3211,3221,3260-3261,3268-3269,3283,3300-3301,3306,3322-3325,3333,3351,3367,3369-3372,3389-3390,3404,3476,3493,3517,3527,3546,3551,3580,3659,3689-3690,3703,3737,3766,3784,3800-3801,3809,3814,3826-3828,3851,3869,3871,3878,3880,3889,3905,3914,3918,3920,3945,3971,3986,3995,3998,4000-4006,4045,4111,4125-4126,4129,4224,4242,4279,4321,4343,4443-4446,4449,4550,4567,4662,4848,4899-4900,4998,5000-5004,5009,5030,5033,5050-5051,5054,5060-5061,5080,5087,5100-5102,5120,5190,5200,5214,5221-5222,5225-5226,5269,5280,5298,5357,5405,5414,5431-5432,5440,5500,5510,5544,5550,5555,5560,5566,5631,5633,5666,5678-5679,5718,5730,5800-5802,5810-5811,5815,5822,5825,5850,5859,5862,5877,5900-5904,5906-5907,5910-5911,5915,5922,5925,5950,5952,5959-5963,5987-5989,5998-6007,6009,6025,6059,6100-6101,6106,6112,6123,6129,6156,6346,6389,6502,6510,6543,6547,6565-6567,6580,6646,6666-6669,6689,6692,6699,6779,6788-6789,6792,6839,6881,6901,6969,7000-7002,7004,7007,7019,7025,7070,7100,7103,7106,7200-7201,7402,7435,7443,7496,7512,7625,7627,7676,7741,7777-7778,7800,7911,7920-7921,7937-7938,7999-8002,8007-8011,8021-8022,8031,8042,8045,8080-8090,8093,8099-8100,8180-8181,8192-8194,8200,8222,8254,8290-8292,8300,8333,8383,8400,8402,8443,8500,8600,8649,8651-8652,8654,8701,8800,8873,8888,8899,8994,9000-9003,9009-9011,9040,9050,9071,9080-9081,9090-9091,9099-9103,9110-9111,9200,9207,9220,9290,9415,9418,9485,9500,9502-9503,9535,9575,9593-9595,9618,9666,9876-9878,9898,9900,9917,9929,9943-9944,9968,9998-10004,10009-10010,10012,10024-10025,10082,10180,10215,10243,10566,10616-10617,10621,10626,10628-10629,10778,11110-11111,11967,12000,12174,12265,12345,13456,13722,13782-13783,14000,14238,14441-14442,15000,15002-15004,15660,15742,16000-16001,16012,16016,16018,16080,16113,16992-16993,17877,17988,18040,18101,18988,19101,19283,19315,19350,19780,19801,19842,20000,20005,20031,20221-20222,20828,21571,22939,23502,24444,24800,25734-25735,26214,27000,27352-27353,27355-27356,27715,28201,30000,30718,30951,31038,31337,32768-32785,33354,33899,34571-34573,35500,38292,40193,40911,41511,42510,44176,44442-44443,44501,45100,48080,49152-49161,49163,49165,49167,49175-49176,49400,49999-50003,50006,50300,50389,50500,50636,50800,51103,51493,52673,52822,52848,52869,54045,54328,55055-55056,55555,55600,56737-56738,57294,57797,58080,60020,60443,61532,61900,62078,63331,64623,64680,65000,65129,65389"/>
<verbose level="0"/>
<debugging level="0"/>
<hosthint>
<status state="up" reason="unknown-response" reason_ttl="0"/>
<address addr="82.180.175.28" addrtype="ipv4"/>
<hostnames>
<hostname name="cyberthreatinsider.com" type="user"/>
</hostnames>
</hosthint>
<host starttime="1750337638" endtime="1750337644">
<status state="up" reason="syn-ack" reason_ttl="0"/>
<address addr="82.180.175.28" addrtype="ipv4"/>
<hostnames>
<hostname name="cyberthreatinsider.com" type="user"/>
</hostnames>
<ports>
<extraports state="filtered" count="984">
<extrareasons reason="host-unreach" count="532" proto="tcp" ports="1,3-4,7,9,13,17,19,24,30,32-33,70,79,85,88,100,109,119,146,163,212,222,254,259,264,311,366,406,425,427,444,465,481,497,500,514,541,544-545,548,563,617,631,636,648,667-668,683,687,691,700,705,711,714,783,787,801,808,843,873,888,898,900-903,912,987,990,992,1001-1002,1009-1011,1021-1024,1026,1028-1030,1032,1035-1036,1039,1041,1043,1046-1048,1054-1056,1059-1061,1063-1064,1066-1067,1069,1072-1077,1079-1085,1089-1093,1096-1097,1099-1100,1104-1106,1110-1111,1113,1117,1121,1126,1132,1137-1138,1149,1151-1152,1154,1163-1166,1169,1174-1175,1183,1187,1192,1198,1213,1216-1218,1233,1244,1247-1248,1259,1272,1277,1287,1296,1300,1309-1311,1322,1328,1433-1434,1455,1500-1501,1583,1600,1658,1666,1717,1719,1755,1805,1812,1839,1863-1864,1900,1914,1935,1947,1971-1972,1999,2001-2002,2004,2006-2007,2010,2013,2030,2033-2035,2038,2041,2045,2065,2103,2105,2111,2119,2121,2126,2144,2160-2161,2190-2191,2196,2260,2288,2323,2366,2381-2383,2393-2394,2492,2522,2557,2602,2604,2608,2638,2701-2702,2710,2717,2811,2909,2967-2968,3001,3003,3005,3011,3017,3030,3052,3168,3269,3283,3300,3322,3325,3351,3367,3369,3372,3404,3517,3527,3551,3580,3659,3690,3737,3766,3800-3801,3809,3826-3827,3851,3880,3971,3995,3998,4000,4005-4006,4111,4125-4126,4129,4242,4279,4321,4343,4449,4662,4848,4900,5000,5003,5033,5060,5080,5087,5102,5200,5221-5222,5225-5226,5269,5357,5405,5431,5440,5510,5544,5560,5633,5679,5718,5730,5800,5850,5859,5862,5902-5904,5907,5915,5925,5950,5959,5961-5963,5987-5988,5999-6002,6005-6007,6009,6025,6106,6123,6129,6389,6547,6567,6646,6667-6669,6692,6779,6788-6789,6839,6969,7000,7002,7004,7019,7025,7070,7100,7103,7402,7435,7496,7512,7625,7627,7676,7741,7800,7911,7920,7937-7938,8002,8010-8011,8031,8045,8082,8086-8087,8090,8093,8099-8100,8193,8200,8254,8290,8300,8333,8400,8500,8654,8899,8994,9000-9001,9009-9010,9040,9050,9080-9081,9090-9091,9099,9102-9103,9207,9220,9290,9415,9418,9503,9575,9593-9594,9666,9917,9929,9968,9998-10002,10025,10082,10180,10566,10621,10626,10629,10778,11111,12265,12345,13456,13783,14238,14441,15000,15004,15660,16000-16001,16012,16016,16018,16113,16992,17877,18040,18988,19101,19315,19780,20000,20031,20221-20222,20828,21571,22939,24444,25734,27000,27352-27353,27355,28201,30000,30718,30951,31038,32769,32772,32775,32780,32782-32783,33899,34572-34573,38292,41511,44442-44443,45100,48080,49153-49155,49158,49163,49165,49167,49400,49999-50002,50006,50389,50636,52673,52822,54045,55055,55600,56737,57797,60020,60443,62078,63331,64680,65000,65389"/>
<extrareasons reason="no-response" count="452" proto="tcp" ports="6,22-23,25-26,37,42-43,49,53,81-84,89-90,99,106,110-111,113,125,135,139,143-144,161,179,199,211,255-256,280,301,306,340,389,407,416-417,445,458,464,512-513,515,524,543,554-555,587,593,616,625,646,666,720,722,726,749,765,777,800,880,911,981,993,995,999-1000,1007,1025,1027,1031,1033-1034,1037-1038,1040,1042,1044-1045,1049-1053,1057-1058,1062,1065,1068,1070-1071,1078,1086-1088,1094-1095,1098,1102,1107-1108,1112,1114,1119,1122-1124,1130-1131,1141,1145,1147-1148,1185-1186,1199,1201,1234,1236,1271,1301,1334,1352,1417,1443,1461,1494,1503,1521,1524,1533,1556,1580,1594,1641,1687-1688,1700,1718,1720-1721,1723,1761,1782-1783,1801,1840,1862,1875,1974,1984,1998,2000,2003,2005,2008-2009,2020-2022,2040,2042-2043,2046-2049,2068,2099,2401,2500,2525,2601,2605,2607,2718,2725,2800,2809,2869,2875,2910,2920,2998,3000,3006-3007,3013,3031,3071,3077,3128,3211,3221,3260-3261,3268,3301,3323-3324,3333,3370-3371,3389-3390,3476,3493,3546,3689,3703,3784,3814,3828,3869,3871,3878,3889,3905,3914,3918,3920,3945,3986,4001-4004,4045,4224,4443-4446,4550,4567,4899,4998,5001-5002,5004,5009,5030,5050-5051,5054,5061,5100-5101,5120,5190,5214,5280,5298,5414,5432,5500,5550,5555,5566,5631,5666,5678,5801-5802,5810-5811,5815,5822,5825,5877,5900-5901,5906,5910-5911,5922,5952,5960,5989,5998,6003-6004,6059,6100-6101,6112,6156,6346,6502,6510,6543,6565-6566,6580,6666,6689,6699,6792,6881,6901,7001,7007,7106,7200-7201,7443,7777-7778,7921,7999-8001,8007-8009,8021-8022,8042,8080-8081,8083-8085,8088-8089,8180-8181,8192,8194,8222,8291-8292,8383,8402,8443,8600,8649,8651-8652,8701,8800,8873,8888,9002-9003,9011,9071,9100-9101,9110-9111,9200,9485,9500,9502,9535,9595,9618,9876-9878,9898,9900,9943-9944,10003-10004,10009-10010,10012,10024,10215,10243,10616-10617,10628,11110,11967,12000,12174,13722,13782,14000,14442,15002-15003,15742,16080,16993,17988,18101,19283,19350,19801,19842,20005,23502,24800,25735,26214,27356,27715,31337,32768,32770-32771,32773-32774,32776-32779,32781,32784-32785,33354,34571,35500,40193,40911,42510,44176,44501,49152,49156-49157,49159-49161,49175-49176,50003,50300,50500,50800,51103,51493,52848,52869,54328,55056,55555,56738,57294,58080,61532,61900,64623,65129"/>
</extraports>
<port protocol="tcp" portid="20">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="ftp-data" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="21">
<state state="open" reason="syn-ack" reason_ttl="0"/>
<service name="ftp" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="80">
<state state="open" reason="syn-ack" reason_ttl="0"/>
<service name="http" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="443">
<state state="open" reason="syn-ack" reason_ttl="0"/>
<service name="https" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2100">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="amiganetfs" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2106">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="ekshell" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2107">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="msmq-mgmt" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2135">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="gris" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2170">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="eyetv" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2179">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="vmrdp" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2200">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="ici" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2222">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="EtherNetIP-1" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2251">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="dif-port" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2301">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="compaqdiag" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="2399">
<state state="closed" reason="conn-refused" reason_ttl="0"/>
<service name="fmpro-fdal" method="table" conf="3"/>
</port>
<port protocol="tcp" portid="3306">
<state state="open" reason="syn-ack" reason_ttl="0"/>
<service name="mysql" method="table" conf="3"/>
</port>
</ports>
<times srtt="10800" rttvar="427" to="100000"/>
</host>
<runstats>
<finished time="1750337644" timestr="Thu Jun 19 13:54:04 2025" summary="Nmap done at Thu Jun 19 13:54:04 2025; 1 IP address (1 host up) scanned in 6.56 seconds" elapsed="6.56" exit="success"/>
<hosts up="1" down="0" total="1"/>
</runstats>
</nmaprun>
Grepable Output
nmap -oG output.gnmap <target>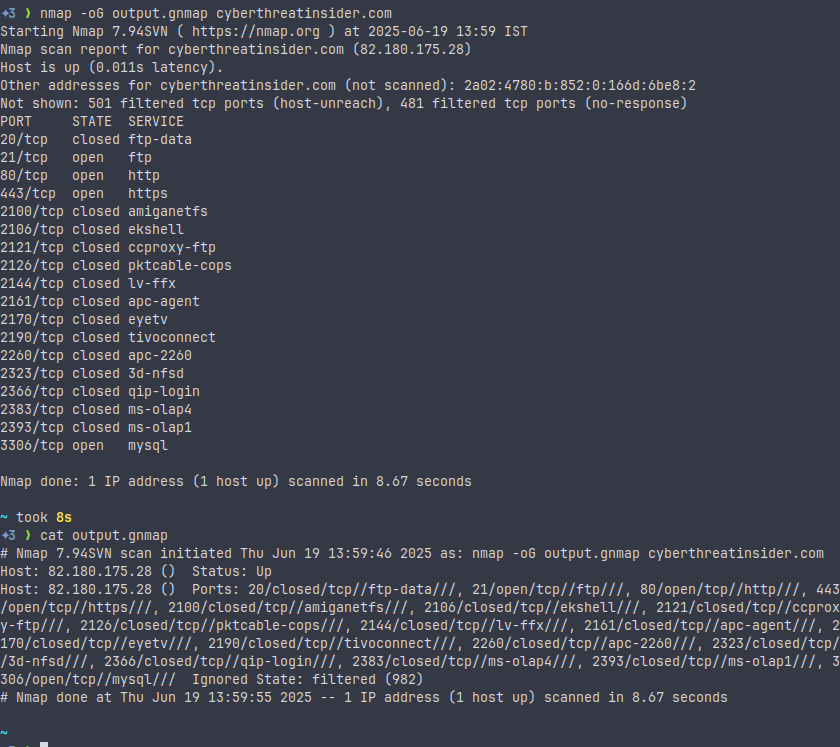
- Format: Line-by-line, grep-friendly format.
- Use case: Ideal for quickly extracting open ports or IP addresses using command-line tools like grep, awk, and cut.
Output All Format
nmap -oN output.txt -oX output.xml -oG output.gnmap <target>This will create:
- A pretty report for reading (output.txt)
- A machine-readable format (output.xml)
- A grep-friendly summary (output.gnmap)
NSE Vulnerability Scan
nmap --script=vuln <target>This command executes an NSE (Nmap Scripting Engine) script to check for known vulnerabilities.
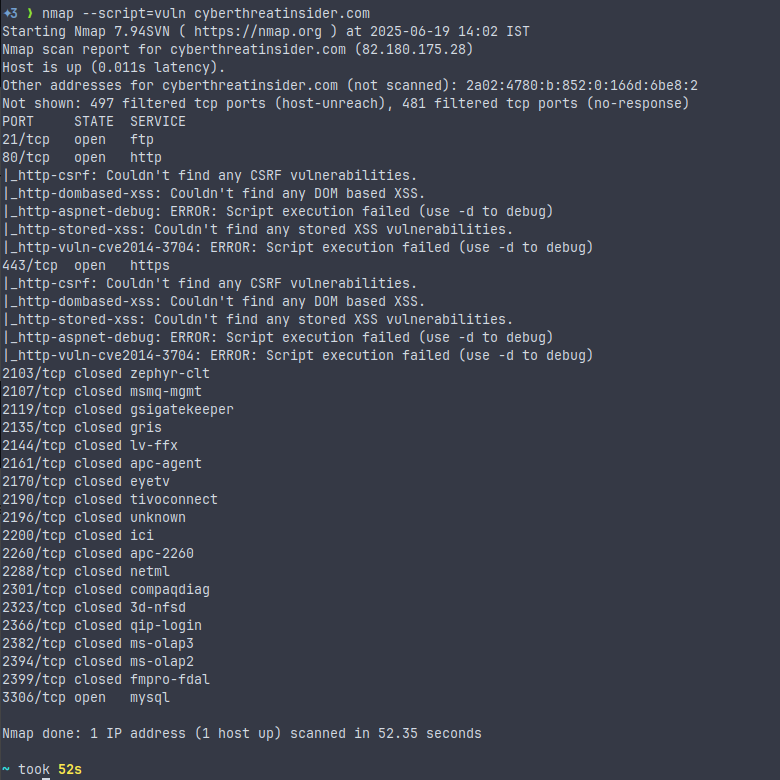
For Example, SMB vulnerabilities (like MS17-010 / EternalBlue), HTTP server misconfiguration, and SSL/TLS weaknesses
NSE Default Scan
nmap --script=default <target>It is a general-purpose information gathering, often part of -A. This command runs the default NSE script set, which includes:
- Service detection (like HTTP headers and SSH banners)
- DNS info
- Basic vulnerability checks
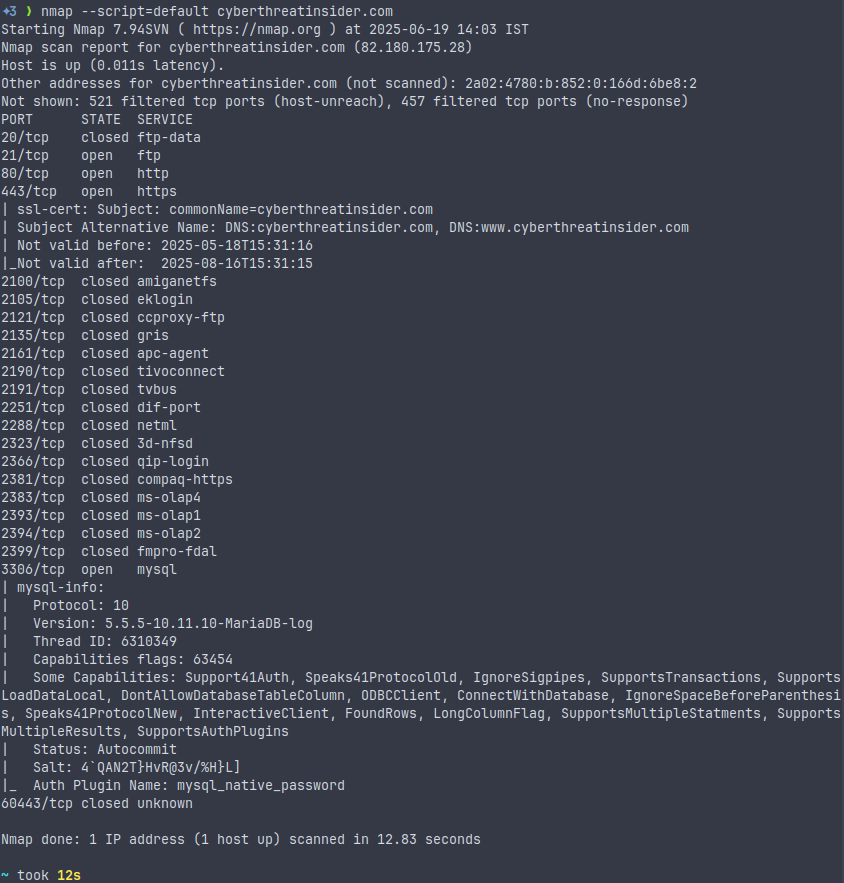
NSE Website Title Grabbing
nmap --script=http-title <target>This command catches the tag from HTTP responses (like a web page’s browser title).
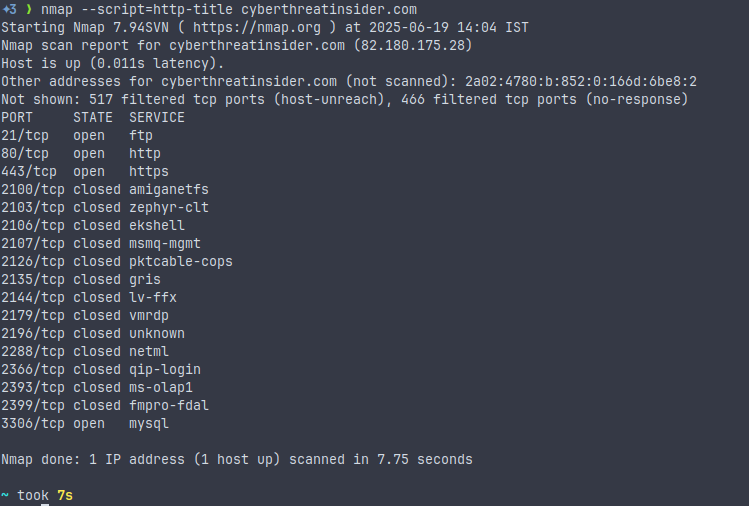
It is useful when scanning multiple hosts to quickly identify websites or services without manually visiting them.
Scan Speed/Timing
nmap -T4 <target>This command sets the scan of speed and aggressiveness. The speed is directly linked to aggressiveness. The faster it is, the noisier it will be.
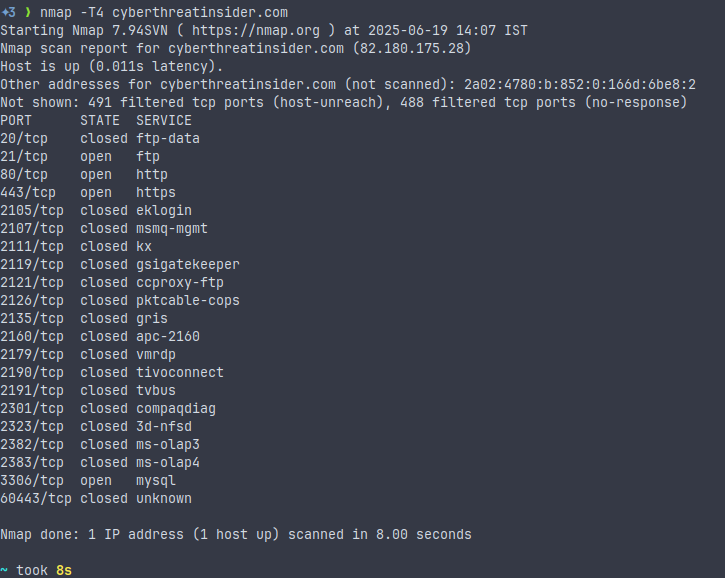
Range: -T0 (slowest) to -T5 (fastest).
- -T3:Defaultt
- -T4: faster, used in LANs or fast networks
- -T5: very aggressive, may trigger IDS
Use case: -T4 is a safe balance between speed and stealth on responsive networks.
No Ping Scan
nmap -Pn <target>This command will skips the host discovery or ping scan. It means all targets are alive (assuming), no need to check.
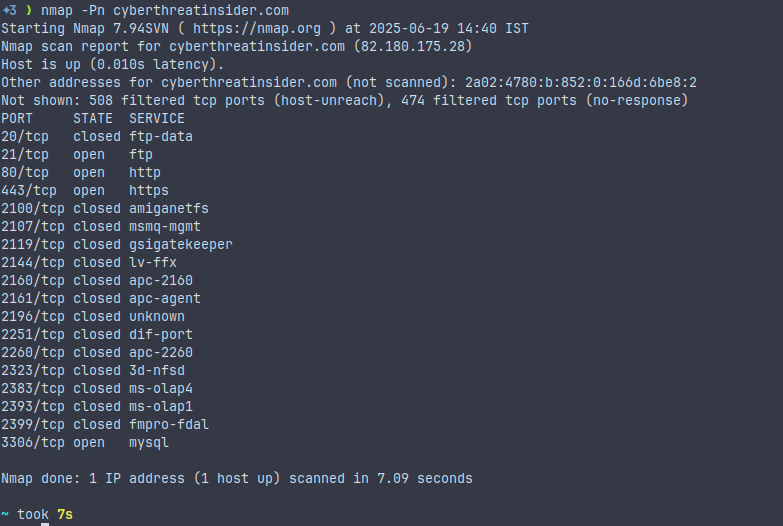
Use case:
- Host is behind a firewall and won’t respond to ping
- You’re scanning internal networks or want to be stealthy
No DNS Resolution
nmap -n <target>This command will prevent the tool from doing reverse DNS lookups.

Use case: Speeds up scans when hostnames are unnecessary (e.g., scanning a large subnet).
Verbose Output
nmap -v <target>This command, will show you the output of the scan in real-time. It is known as verbosity.
Use multiple -v flags (-vv) for even more verbosity.

Use case: Helpful for seeing real-time progress, especially on long scans.
IPv6 Scanning
nmap -6 <target>This command enables the scanning of IPv6 addresses.
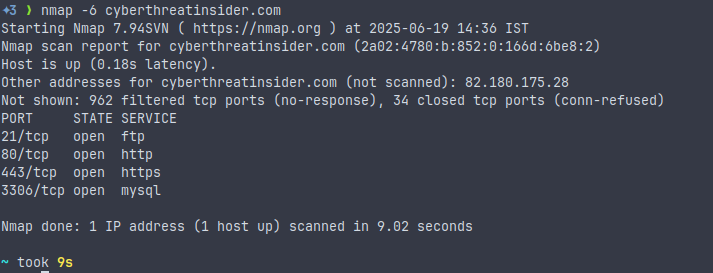
Use case: When scanning targets that only have or support IPv6.
There’s a catch, you need to give an actual IPv6 address; it won’t work with IPv4-style input.
Conclusion
These 30 commands give you a solid foundation, but Nmap is just the tip of the iceberg. As you grow more comfortable, dive into the powerful Nmap Scripting Engine (NSE) or automate scans with your scripts. Just remember: always scan with permission!
Be aware not to use aggressive scanning on any target, as it is easily detected by firewalls or Intrusion Detection Systems/Intrusion Prevention Systems (IDS/IPS).


